Configuration convertor from PICOS to SONiC
This configuration converter is intended for network administrators with PICOS background. This guide will help network admins to migrate their current PICOS deployment for various Fabric architectures to SONiC. PICOS User guide https://docs.pica8.com/ can be used as a checklist to get started with the migration plan from PICOS to SONiC. Following document provides example configuration commands for comparison.
Switch Management
Operator has to login to PICOS and SONiC switch as super user using “sudo su”
| PICOS | SONiC |
|---|---|
| Management IP | |
|
# OOB Management IP # Syntax set system management-ethernet <mgmt-if> ip-address IPv4 <ip-address> run show system management-ethernet #Example set system management-ethernet eth0 ip-address IPv4 192.168.10.5/24 #Inband Management IP #Syntax set system inband vlan-interface <vlan-interface-name> set system inband loopback <ip-address> set system inband routed-interface <routed-interface-name> #Example set system inband vlan-interface VLAN400 set system inband loopback 192.168.10.1 set system inband routed-interface rif-ge3 |
# OOB Management IP #Syntax config interface ip add <mgmt-if> <Ipv4_address> / <Ipv4_subnet> <gateway_ipv4_address> #Example config interface ip add eth0 192.168.1.1/24 192.168.1.254 # OOB Management IP with VRF #Syntax config VRF add mgmt config interface ip add mgmt <VRF-NAME> Ipv4_address>/ <Ipv4_subnet> <gateway_IPV4_address> #Example config VRF add mgmt config interface ip add mgmt VRF-1 192.168.1.1/24 192.168.1.254 # Command to verify management ip address configured show management_interface address Management IP address = 192.168.1.1/24 Management Network Default Gateway = 192.168.1.254 |
| Switch Reboot | |
|
#Command in PICOS to reboot system but it will cause traffic disruption request system reboot # Command sets the system log file to save to disk. set system syslog local-file disk tail -f /var/log/messages |
#Command to perform system reboot which cause some disruption of data traffic - reboot #Command defines the cause of reboot of a sonic device show reboot-cause show reboot-cause history #Command enables a switch to reboot up quickly with minimum disruption to the data plane. fast-reboot #Warm reboot commands perform in-service NOS upgrade without impacting the data plane traffic warm-reboot -v config warm_restart enable/disable config warm_restart enable # Command shows configuration of warm restart setting and show whether that service is enabled or disabled show warm_restart config show warm_restart state # Command to view syslogs tail -f /var/log/syslog |
| Upgrade NOS | |
|
#Command to check the version in PICOS Version #Command to upgrade the version in PICOS upgrade upgrade [image_name] [factory-default] [backup-file=(*.lst)] image_name - Image with bin format file(*.bin) factory-default - Recovery configuration to factory default backup-file=(*.lst) - Specify a user defined backup list upgrade backup-file=/admin/back_files.lst onie-installer-picos-4.0.1-x86.bin Sync # Example upgrade onie-installer-picos-4.0.1-x86.bin |
#Syntax #Command to check the version in SONiC Show version #Command to upgrade the version in SONiC sonic-installer sonic-installer install sonic-installer install [OPTIONS] <image_file_path> sonic-installer list # Command to set which image will be used for default boot image after any system reboot sonic-installer set-default sonic-installer set-default <image_name> sonic-installer set-next-boot # Operator can use following command to remove a saved sonic image in device flash/disk - sonic-installer remove sonic-installer remove [y|-yes] <image_name> |
| Configuration Save | |
|
# Command to save the configuration on PICOS save myconfig.conf # CLI to delete and re-add a new save config - load override myconfig.conf # Merge a new config on top of existing running configuration – load merge myconfig.conf |
# Command to save the configuration on SONiC config save -y # Command to delete and re-add a new save config - config reload <config_db.json/SONiCYang> # Command to load the configuration from json.db config load <config json file> # Replace a new configuration on top of existing running configuration - config replace <config_db.json/SONiCYang> |
| Platform Information | |
|
#Platform show commands #syntax run show system serial-number run show system rpsu run show system serial-number run show system temperature run show system uptime run show system connections run show system core-dumps run show system cpu-usage run show system rpsu run show system date run show system fan run show system memory-usage run show system name run show system temperature run show system users |
#Command to verify platform details in SONiC
#Syntax show system Status show clock show boot show environment show system status show reboot-cause show uptime show logging show users show platform fan show platform firmware status show platform firmware version show platform pcieinfo show platform psustatus show platform ssdhealth show platform summary show platform syseeprom show platform temperature show interfaces transceiver |
Management Services
| PICOS | SONiC |
|---|---|
| SYSLOG | |
|
#Syslog commands in PICOS #Syntax set system log-level info syslog monitor on set protocols OSPF traceoptions packet all detail set system log-level trace commit syslog monitor on |
#Syslog commands in SONiC #Syntax config syslog add config syslog delete #Command to add or delete a specific syslog server IP config syslog add <ipv4-address> --source <source_ipv4_address></config> config syslog del <ipv4-address> #View syslog for a particular protocol in SONIC - show logging show logging <any_protocol> # Command to show syslog server IP and port configuration show syslog #Location of syslog configuration file - Configuration file for syslog available at: /etc/rsyslog.conf #Example Configuration config syslog add 1.1.1.1 --source 192.168.8.231 config syslog del 1.1.1.1 # Command to view syslog file location Path: /var/log/syslog* |
| ZTP | |
|
# Configuration to enable and disable Zero Touch Provisioning # Syntax ztp-config Please configure the default PicOS ZTP options: (Press other key if no change) [1] PicOS ZTP enabled * default [2] PicOS ZTP disabled Enter your choice (1,2):2 PicOS ZTP is disabled. admin@LEAF-A$ # Alternative Method is to edit the PICOS configuration file picos_start.conf and change the value of the ztp_disable variable. admin@LEAF-A$more /etc/picos/picos_start.conf | grep ztp ztp_disable=true # To enable ZTP, the user needs to set ztp_disable to false. |
#Configuration
#Syntax #Enable the ZTP services admin@sonic:~$ config ztp enable # Running the ZTP Services admin@sonic:~$ config ztp run -y #Check the ZTP Status admin@sonic:~$ show ztp status #Check the /etc/sonic , user will be able to see config_db.json admin@sonic:~$ ls /etc/sonic/ | grep config_db.json Config_db.json # Server where ZTP server is hosted , operator can edit in a customized way various parameters like URL , source path location , destination path location during ZTP automated discovery process. #Using ZTP to download the config_db.json and the new SONiC version. #Example Example for ztp.json.
{
"ztp": {
"01-configdb-json": {
"url": {
"source": "tftp://188.188.36.36/7326_56X_config_db.json",
"destination": "/etc/sonic/config_db.json"
}
},
"02-firmware": {
"install": {
"url": "http://188.188.36.36:8000/sonic-broadcom.bin",
"skip-reboot": true
}
}
}
}
|
| SNMP | |
|
# Add SNMP Community and Agent Address ovs-vsctl set-snmp-enable true ovs-vsctl show-snmp snmp is enabled ovs-vsctl set-snmp-community-name pica8 ovs-vsctl set-snmp-community-name #Syntax # Add SNMP traps and SNMP server target address - ovs-vsctl show-snmp-trap-targets ovs-vsctl set-snmp-trap-targets <Server_IP_Address> ovs-vsctl set-snmp-trap-targets |
# SONiC - Add SNMP Community and Agent Address #syntax config snmp community add <snmp_community_name> <Mode_Readonly or read Write> #Example config snmp community add testcomm ro # Command to add SNMP Agent IP address config snmpagent add <Agent_IPV4_Address> -v <VRF-NAME> # Command to add SNMP user #Syntax config snmp user add <user> (noAuthNoPriv | AuthNoPriv | Priv) (RO | RW) [[(MD5 | SHA | MMAC-SHA-2) <auth_password>] [(DES |AES) <encrypt_password>]] #Example config snmp user add testuser3 priv rw md5 testuser3_auth_pass aes testuser3_encrypt_pass # Add SNMP traps and SNMP server target address - config snmptrap modify 2 <Server_IP_Address> show snmptrap show snmp agentaddress show running configuration snmp |
| AAA/Radius | |
|
# Configure Radius Server IP and Port set system aaa radius authorization disable <true | false> set system aaa radius authorization server-ip <ipv4_address> set system aaa radius authorization server-ip <:ipv4_address> port <integer> set system aaa radius source-interface <interface-name> # Show- show system aaa radius Enable RADIUS accounting - set system aaa radius accounting disable <true | false> set system aaa radius accounting server-ip |
# SONiC - Configure Radius Server IP and Port #Syntax config aaa authentication login {radius | tacacs+ | local} [radius | tacacs+ | local]. config radius add <Radius_server_ip> #Show Radius commands- show aaa show radius #Command for aaa authentication options #Syntax aaa authentication login tacacs+ # If one AAA server fails , go to backup AAA server for authentication aaa authentication failthrough <enable/disable/default> aaa authentication fallback <enable/disable/default> # AAA accounting enable commands in SONiC #Syntax config aaa accounting local config aaa accounting tacacs+ # Command to add aaa accounting server IP and bind it to a data interface config radius add <accounting_server_ip> config radius add <accounting_server_ip> --s <source_interface> |
| sFlOW | |
|
#sflow commands ovs-vsctl --id=@s create sFlow agent=eth0 target="10.10.50.207:9901" header=128 sampling=5000 polling=30 -- set Bridge br0 sflow=@s ovs-vsctl list sflow ovs-vsctl -- clear Bridge br0 sflow |
# Command to add sflow collector config sflow collector add <collector_name1> <sflow_collector_ipv4> <port_number> config sflow collector add <collector_name2> <sflow_collector_ipv6> <port_number> # Command to delete sflow collector config sflow collector del <collector-name1> config sflow collector del <collector-name2> # Command to add and delete sflow agent config sflow agent-id add config sflow agent-id del # Command to bind sflow agent to an interface config sflow agent-id add <Ethernet_interface_number> config sflow agent-id add <loop_interface_number> # Command Enable / Disable sflow - config sflow enable config sflow disable config sflow interface config sflow interface <enable/disable> config sflow interface enable <Ethernet_interface> # Configure sflow sample rate , interval config sflow interface sample-rate <interface_name> <sample_rate> config sflow polling-interval # Command to show sflow configuration - show sflow show sflow interface |
| NTP | |
|
# Configuring the NTP Server IP Address set system ntp server-ip <NTP_SERVER_IP> # Configuring NTP Source Interface set system ntp source-interface <VLAN-INTERFACE-NUMBER> #Configuring Time Zone set system timezone <TIME_ZONE> #Configuring System Clock set date YYYY:MM:DD -TT |
# Command to configure NTP Server IP #Syntax config ntp add <NTP_SERVER_IP> # Example config ntp add 100.100.10.10 # Command to delete a configure NTP Server IP config ntp del <ip_address> #restart NTP-config daemon after applying NTP server config through config_db.json systemctl restart ntp-config # Command to list system timezone. timedatectl list-timezones #Command to modify the time zone timedatectl set-timezone <TIME_ZONE> #Command to show the NTP server information show ntp |
Port Mirroring
| PICOS | SONiC |
|---|---|
|
#Configuring port as port mirroring #Syntax set interface ethernet-switching-options analyzer 111 output ge-<x/y/z> # Configure Monitor the flows of ingress port set interface ethernet-switching-options analyzer <number> input ingress ge-x/y/z # Configure Monitor the Flows of Egress Port set interface ethernet-switching-options analyzer <number> input egress ge-<x/yz> #Configuring Mirroring on Egress or Ingress Port set interface ethernet-switching-options analyzer <number> input ingress ge-<x/y/z> set interface ethernet-switching-options analyzer |
#Create a mirror session #Syntax config mirror_session add ts1_everflow <Source_Ip_address> <destination_Ip_Address> <dscp_number> <queue_number> # Command to create ACL table config acl add table ACL_Mirror MIRROR --description 'mirror' --stage ingress --ports Ethernet0 # Command an ACL JSON file and load it to the configuration database for everflow. cat acl.json
{
"ACL_RULE": {
"ACL_Mirror|ACE_Mirror": {
"PRIORITY": "55",
"IP_TYPE": "ipv4any",
"MIRROR_ACTION": "ts1_everflow"
}
}
}
# Command to load the acl.json with new config related to ACL applied
config load acl.json -y#Command to verify the mirror status show mirror_session # Command to create a mirror session for SPAN #Syntax config mirror_session span add <session_name> <Destination_interface_Analyzer> <Source_intertface_switch> # Command to create a mirror session for Remote SPAN config mirror_session erspan add <session_name> <src_ip> <dst_ip> <dscp> <ttl> [gre_type] [queue] [src_port] [direction] #Command to create a mirror session and ACL table config mirror_session span add <session_name> <Destination_port> <Source_port> <Direction> # Example config acl add table Test MIRROR -p Ethernet8 -s ingress #Command to verify the mirror table show mirror_session # Create ACL JSON file and load it to the configuration database for Mirror cat acl.json
{
"ACL_RULE": {
"Test|Forward": {
"PRIORITY": "2",
"MIRROR_ACTION": "test",
"VLAN_ID": "20"
}
}
}
# Command to load the json file with ACL config appliedconfig load acl.json -y config save -y #Command to check the status of ACL table and mirror session show mirror_session show acl table |
Layer 2 Switching
Interface and port VLAN
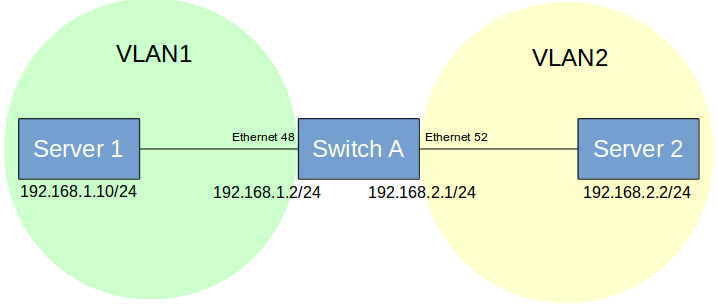
| PICOS | SONiC |
|---|---|
| Port, VLAN | |
|
#Configure Access and Trunk Mode over interfaces set interface gigabit-ethernet <ethernet_interface> family ethernet-switching port-mode access set interface gigabit-ethernet <ethernet_interface> family ethernet-switching port-mode trunk # Create VLANs set vlans vlan-id <vlan_value> run show vlans # Add VLAN members to ethernet ports for tagged packet set interface gigabit-ethernet <ethernet_interface> family ethernet-switching vlan members <vlan_member1> set interface gigabit-ethernet <ethernet_interface> family ethernet-switching vlan members <vlan_member2> # Add VLAN members to ethernet ports for untagged packet set interface gigabit-ethernet <ethernet_interface> family ethernet-switching vlan members <member1> untagged set interface gigabit-ethernet <ethernet_interface> family ethernet-switching vlan members <member2> untagged |
#Configure Access and Trunk Mode over interfaces config interface speed Ethernet<interface> <speed> config interface advertised-speeds Ethernet<interface> <speed> #Command to set Auto Negotiation for an ethernet interface config interface autoneg Ethernet<interface> enable #Command to show status of Auto Negotiation for an ethernet interface show interface autoneg status Ethernet0 #Command to show operational status of interface show interface status #Example command to configure 4x10GE breakout for a 40GE port config interface breakout Ethernet1 '4x10G' #Command to show interface breakout options show interface breakout #Command to configure FEC mode of an ethernet interface config interface fec Etherne<interface> <FEC_MODE> # Create VLANs config vlan add <vlan_value1> config vlan add <vlan_value2> # show vlan configuration show vlan config #Add Interface to vlan in Tagged (Trunk) mode: config vlan member add <vlan_value1> Ethernet<interface1> config vlan member add <vlan_value2> Ethernet<interface2> #Add Interface to vlan in untagged (access) mode: config vlan member add -u <vlan_value1> Ethernet<interface1> config vlan member add -u <vlan_value2> Ethernet<interface2> #Command to show vlan information show vlan brief |
| LAG | |
|---|---|
|
#Command to create static LAG in an aggregated interface ae1 #Syntax ovs-vsctl add-port br0 ae1 vlan_mode=trunk tag=1 -- set Interface ae1 type=pica8_lag ovs-vsctl -- set Interface ae1 options:lag_type=static ovs-vsctl -- set Interface ae1 options:members=ge-x/x/x , ge-x/x/x #Command to create dynamic LACP in an aggregated interface ae1 set interface aggregate-ethernet ae1 aggregated-ether-options lacp enable true set interface aggregate-ethernet ae1 aggregated-ether-options min-selected-port <number_of_ports> set interface gigabit-ethernet ge-x/x/x ether-options 802.3ad ae1 set interface gigabit-ethernet ge-x/x/x ether-options 802.3ad ae1 set interface gigabit-ethernet gge-x/x/x ether-options 802.3ad ae1 set interface gigabit-ethernet ge-x/x/x ether-options 802.3ad ae1 Commit #Command to display LACP LAG information run show interface aggregate-ethernet ae1 #Configure one LAG ae1 with three memberports. set interface gigabit-ethernet ge-x/y/z ether-options 802.3ad ae1 set interface gigabit-ethernet ge-x/y/z ether-options 802.3ad ae1 set interface gigabit-ethernet ge-x/y/z ether-options 802.3ad ae1 |
#Create port channel #syntax config portchannel add PortChannel<Channel1> #Add members to port channel config portchannel add PortChannel<Channel1> Ethernet<interface> # Command to verify port channel interface show interface portchannel # Command to show vlan status show vlan brief # Command to show ip interface status show ip interfaces show interfaces status #Command to create a PortChannel interface and set the specific LACP key. config portchannel add PortChannel<Channel1> --lacp-key <Key-number> config portchannel member add PortChannel<Channel1> Ethernet<interface> #Command to create a PortChannel interface in fast rate mode config portchannel add PortChannel<number> --fast-rate true #Command to create a PortChannel interface in static mode config portchannel add PortChannel<interface> --static true #Command to add member ports to PortChannel interface config portchannel member add PortChannel<number> Ethernet<interface1> config portchannel member add PortChannel<number> Ethernet<interface2> # Save the setting to config_db.json config save -y #Add member ports to PortChannel interface config portchannel member add PortChannel<interface> Ethernet<interface1> config portchannel member add PortChannel<interface> Etherne<interface2> # Command to show interface portchannel show interfaces portchannel |
| PICOS | SONiC |
|---|---|
| FDB/MAC | |
|
# Command for MAC Learning Configurations- set interface ethernet-switching-options mac-table-aging-time <timer> #Command to show MAC entries learned run show ethernet-switching table |
#Display the MAC (FDB) entries show mac #Display the MACs learned on the particular VLAN ID show mac -v <vlan_value> #Display the MACs learned on the particular port show mac -p Ethernet<interface> #Clear the MAC (FBD) table sonic-clear FDB all #Check MAC aging time show mac aging-time |
Multi-Chassis Link Aggregation Group (MC-LAG)
This is a pair of links that terminates on two cooperating switches and appears as an ordinary link aggregation group (LAG).
Layer 2 Multi Chassis LAG
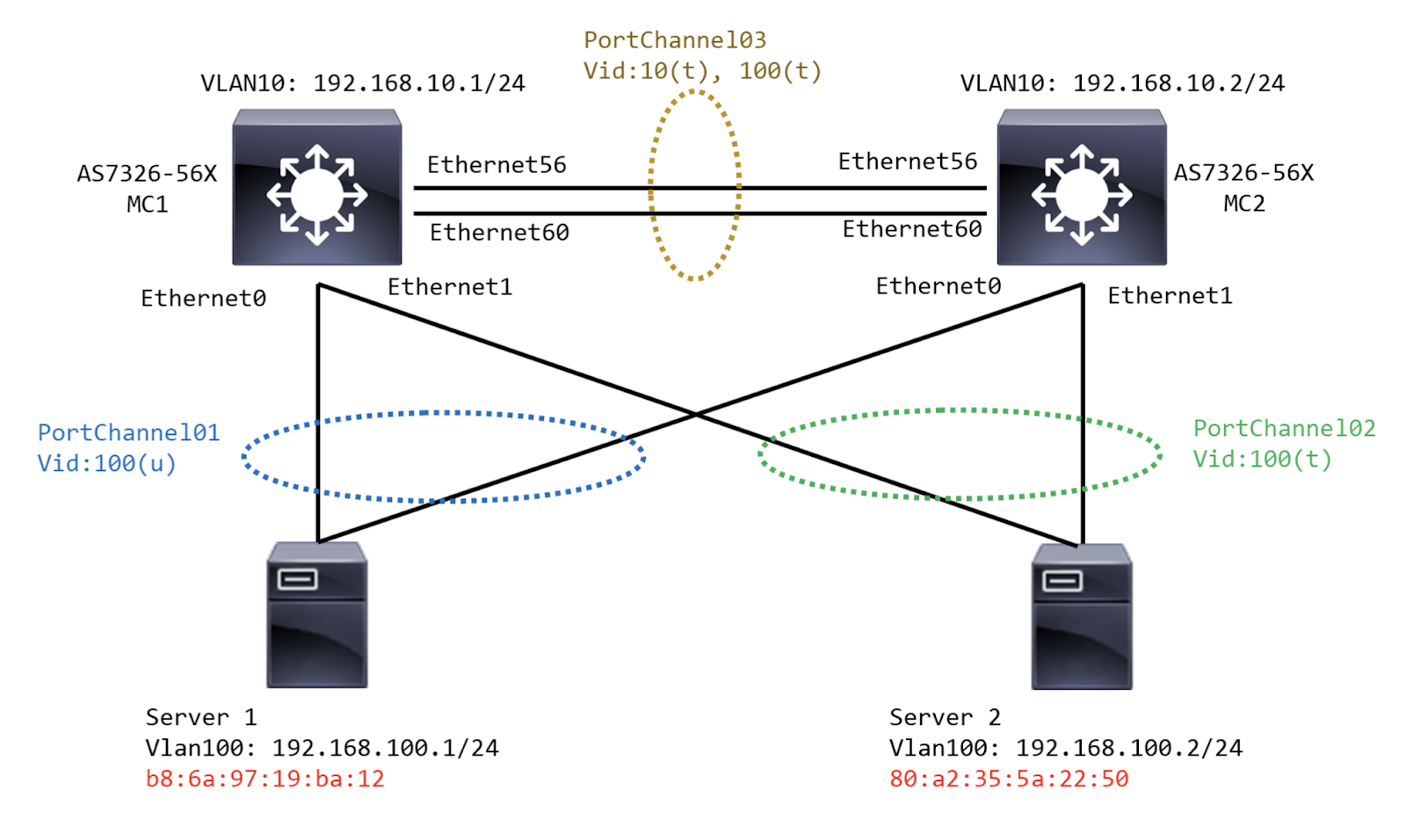
| PICOS | SONiC |
|---|---|
| PortChannel(LACP) and Member | |
|
# Enable LACP set interface aggregate-ethernet <lag-if-name> aggregated-ether-options lacp enable true # Add members set interface gigabit-ethernet <port-id> ether-options 802.3ad ae1 |
#Add Port Channel config port channel add <PCH ID> #Add Members config port channel member add <PCH-ID> <member-port> |
| MC-LAG | |
|
#MCLAG Domain set protocols mlag domain set protocols mlag domain #MCLAG PEER set protocols mlag domain <domain-id> interface <lag-interface> link <link-id> set protocols mlag domain <domain-id> peer-ip <peer-ipv4-address> peer-link <peer-interface-name> set protocols mlag domain <domain-id> peer-ip <peer-ipv4-address> peer-vlan <vlan-id> #MCLAG Members set interface gigabit-ethernet #MCLAG Show run show mlag link { |
#MCLAG Domain & Peer Configuration config interface ip add <VLAN ID> <SVI-IP> config mclag add <mclag-id> <local-ip> <remote-ip> <peer-pch> config mclag unique-ip add <peer-vlan> #MCLAG Members config mclag member add <mclag-id> <member-pch> #MCLAG Show show mclag brief Show mac |
| VLAN | |
|
#VLAN Configuration set vlans vlan-id set interface aggregate-ethernet <lag-if> family ethernet-switching port-mode trunk set interface aggregate-ethernet <lag-if> family ethernet-switching vlan members <vid> |
#VLAN Configuration config vlan add <id> config vlan member add <vid> <pch-id> |
Creating port channel on the MCLAG pair switches running SONiC
config portchannel add PortChannel01
config portchannel add PortChannel02
config portchannel add PortChannel03
config portchannel member add PortChannel01 Ethernet0
config portchannel member add PortChannel02 Ethernet1
config portchannel member add PortChannel03 Ethernet56
config portchannel member add PortChannel03 Ethernet60
Creating VLAN interface on MC LAG pair switches running SONiC
config vlan add 10
config vlan add 100
config vlan member add 10 PortChannel03
config vlan member add -u 100 PortChannel01
config vlan member add 100 PortChannel02
config vlan member add 100 PortChannel03
Configure MCLAG pair switches with domain ID and child member links
config mclag add 1 192.168.10.1 192.168.10.2 PortChannel03
config mclag unique-ip add Vlan10
config mclag member add 1 PortChannel01
config mclag member add 1 PortChannel02
SONiC configuration for MC LAG peer health check
config interface ip add Vlan10 192.168.10.1/24
config interface ip add Vlan10 192.168.10.2/24
SONiC Command to Display MC LAG operationalstatus
show mclag brief
SONiC command to show MAC address learned for host traffic through member link interfaces
show mac
No. Vlan MacAddress Port Type
----- ------ ----------------- ------------- -------
1 10 68:21:5F:29:C0:D2 PortChannel03 Static
2 100 B8:6A:97:19:BA:12 PortChannel01 Dynamic
3 100 80:A2:35:5A:22:50 PortChannel02 Dynamic
Total number of entries 3
Layer 3 Multi Chassis LAG
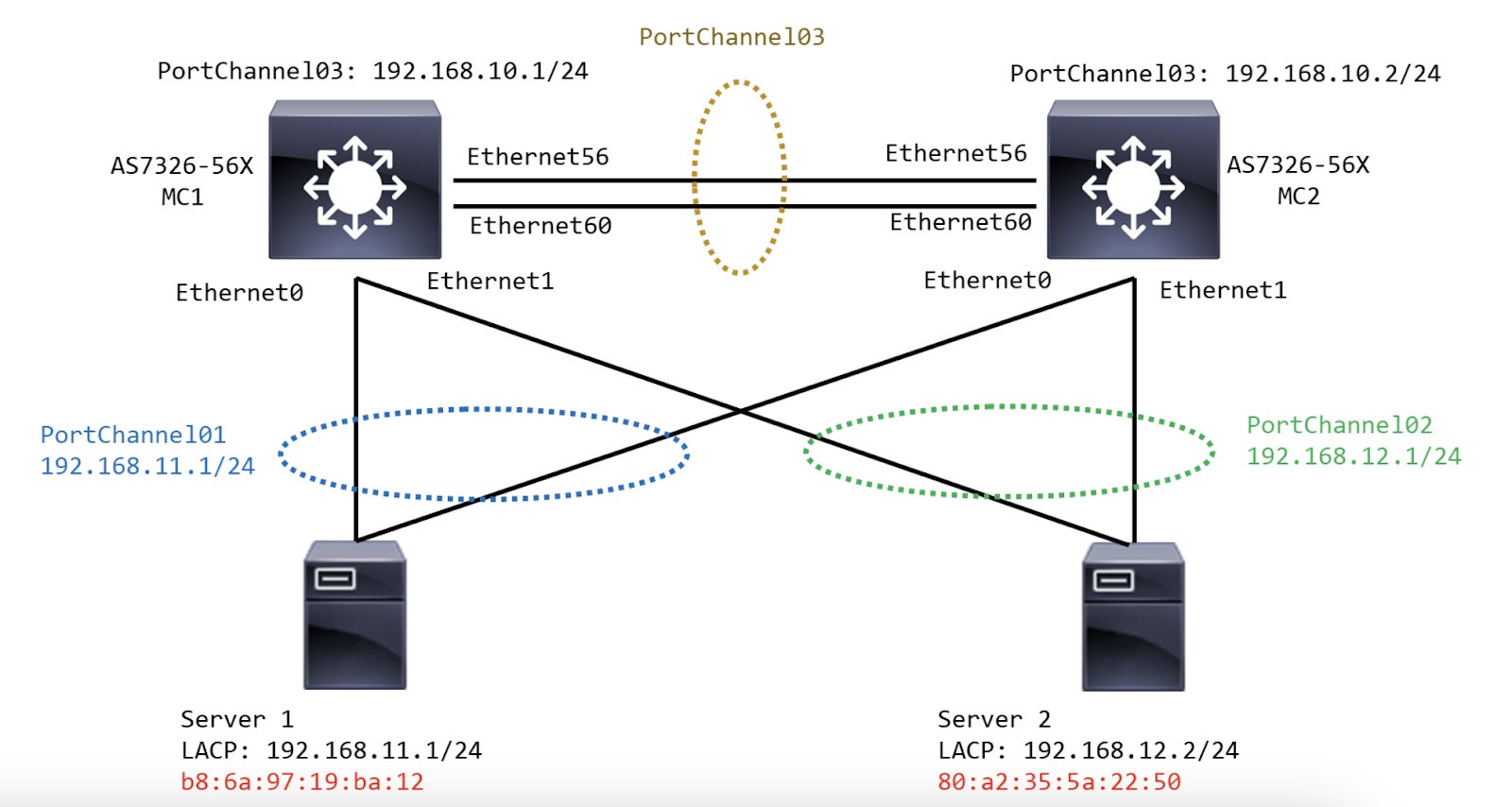
Command to create PortChannel on MC LAG Pair switches
config portchannel add PortChannel01
config portchannel add PortChannel02
config portchannel add PortChannel03
config portchannel member add PortChannel01 Ethernet0
config portchannel member add PortChannel02 Ethernet1
config portchannel member add PortChannel03 Ethernet56
config portchannel member add PortChannel03 Ethernet60
Commands to Create Port Channel IPs on MC LAG pair switches
config interface ip add PortChannel01 192.168.11.1/24
config interface ip add PortChannel02 192.168.12.1/24
config interface ip add PortChannel03 192.168.10.1/24
config interface ip add PortChannel01 192.168.11.1/24
config interface ip add PortChannel02 192.168.12.1/24
config interface ip add PortChannel03 192.168.10.2/24
Command to configure MCLAG on MC LAG pair switches (Domain ID, VLANs and MLAG members)
config mclag add 1 192.168.10.2 192.168.10.1
config mclag member add 1 PortChannel01
config mclag member add 1 PortChannel02
config mclag add 1 192.168.10.1 192.168.10.2
config mclag member add 1 PortChannel01
config mclag member add 1 PortChannel02
SONiC command to Configure IP for MCLAG Peer health check on MC LAG peers
config interface ip add Vlan10 192.168.10.1/24
config interface ip add Vlan10 192.168.10.2/24
Command to show MCLAG Status MC1 switch configuration -
show interfaces portchannel
Flags: A - active, I - inactive, Up - up, Dw - Down, N/A - not available,
S - selected, D - deselected, * - not synced
No. Team Dev Protocol Ports Oper Key Admin Key Fast Rate
----- ------------- ----------- --------------------------- ---------- ----------- -----------
01 PortChannel01 LACP(A)(Up) Ethernet0(S) 101 auto false
02 PortChannel02 LACP(A)(Up) Ethernet1(S) 102 auto false
03 PortChannel03 LACP(A)(Up) Ethernet60(S) Ethernet56(S) 103 auto false
show mclag brief
Domain ID : 1
Role : Active
Session Status : Up
Peer Link Status :
Source Address : 192.168.10.1
Peer Address : 192.168.10.2
Peer Link :
Keepalive Interval : 1 secs
Session Timeout : 15 secs
System MAC : 00:a0:c9:00:00:00
Number of MCLAG Interfaces : 2
MCLAG Interface Local/Remote Status
PortChannel01 Up/Up
PortChannel02 Up/Up
MC2 switch configuration -
admin@sonic:~$ show interfaces portchannel
Flags: A - active, I - inactive, Up - up, Dw - Down, N/A - not available,
S - selected, D - deselected, * - not synced
No. Team Dev Protocol Ports Oper Key Admin Key Fast Rate
----- ------------- ----------- --------------------------- ---------- ----------- -----------
01 PortChannel01 LACP(A)(Up) Ethernet0(S) 101 auto false
02 PortChannel02 LACP(A)(Up) Ethernet1(S) 102 auto false
03 PortChannel03 LACP(A)(Up) Ethernet60(S) Ethernet56(S) 103 auto false
admin@sonic:~$ show mclag brief
Domain ID : 1
Role : Standby
Session Status : Up
Peer Link Status :
Source Address : 192.168.10.2
Peer Address : 192.168.10.1
Peer Link :
Keepalive Interval : 1 secs
Session Timeout : 15 secs
System MAC : 00:a0:c9:00:00:00
Number of MCLAG Interfaces : 2
MCLAG Interface Local/Remote Status
PortChannel01 Up/Up
PortChannel02 Up/Up
SONiC Command to verify ARP synchronization
mclagdctl dump arp -i 1
No. IP MAC DEV Flag
1 192.168.12.2 80:a2:35:5a:22:50 PortChannel02 R
2 192.168.11.2 b8:6a:97:19:ba:12 PortChannel01 L
Link Layer Discovery protocol
LLDP is a standard link-layer discovery protocol which can broadcast its capability, IP address, ID, and interface name as TLVs (Type/Length/Value) in LLDP PDUs (Link Layer Discovery Protocol Data Units).
| PICOS | SONiC |
|---|---|
|
#Command to validate the LLDP status show protocols lldp #Command to Enable LLDP service: set protocols lldp enable true #Command to Configure LLDP information set protocols lldp interface <interface_name> working-mode tx_rx set protocols lldp tlv-select mac-phy-cfg true set protocols lldp tlv-select management-address true set protocols lldp tlv-select port-description true set protocols lldp tlv-select system-capabilities true |
#Command to Enable / Disable LLDP globally config feature state lldp enabled config feature state lldp disabled #Command to Configure LLDP information config lldp global hello_timer <timer_value> config lldp global management_ip <switch_mgmt_ip> config lldp global system_description AS5835-Leaf1 config lldp global system_name<LEAF1> #Command to validate the LLDP status show feature status lldp show lldp table show lldp neighbors show lldp global #Command to enable/disable LLDP over local interfaces docker exec -i lldp lldpcli configure ports Ethernet<interface> lldp status disable configure ports Ethernet<interface> lldp status enable |
Layer 3 Routing
Routed Interface
| PICOS | SONiC |
|---|---|
|
# Configuring Routed Interface # Enable Ethernet port as a layer 3 routed interface. set interface gigabit-ethernet <interface-name> routed-interface enable <true | false> set interface gigabit-ethernet <interface-name> routed-interface name <string> # Command to bring up the parent routed interface. set l3-interface routed-interface <interface-name> # Enable IP routing to perform layer 3 forwarding. set ip routing enable true # Configuring Sub-interface set vlans vlan-id <vlan-id> set interface gigabit-ethernet <interface-name> routed-interface sub-interface <sub-interface-name> vlan-id <vlan-id> set l3-interface routed-interface <interface-name> address <ip-address> prefix-length <prefix-number> # Checking the Configuration run show interface routed-interface brief run show l3-interface routed-interface <interface-name> |
#Command to add a Layer3 Interface address on physical interface - # Configure physical interface IP config interface ip add Ethernet<Number1> <IP_ADDRESS> config interface ip add <vlan_number> <IP_ADDRESS> #Example config interface ip add Loopback<Number> 10.0.2.1/32 config interface ip add Ethernet0 172.16.10.1/31 config interface ip add Vlan100 18.0.0.1/24 # Command to create a sub-interface config interface ip add Ethernet<interace_number>.<vlan-id> <IP_ADDRESS> #Example config interface ip add Ethernet0.10 192.168.10.2/24 # Validate sub-interface operational status show subinterfaces status |
SVI & DHCP Relay:
| PICOS | SONiC |
|---|---|
| SVI | |
|
# Create VLAN IDs #Syntax set vlans vlan-id <vlan1> set vlans vlan-id <vlan2> # Create an interface binded to Layer3 VLAN set interface gigabit-ethernet ge-x/y/z family ethernet-switching native-vlan-id <vlan1> set interface gigabit-ethernet ge-x/y/z family ethernet-switching native-vlan-id <vlan2> # Create Layer 3 VLAN IDs #Syntax set vlans vlan-id<vlan1> l3-interface vlan-<number1> set vlans vlan-id set vlan-interface interface vlan-<number1> vif vlan-<number1> address <ip_address1> prefix-length <subnet> set vlan-interface interface vlan-<number1> vif vlan-<number1> address <ip_address2>1 prefix-length <subnet> # Verify Layer3 interface run show vlan-interface #Verify Ip routes run show ip routes |
# Create VLANs config vlan add <vlan_value1> config vlan add <vlan_value2> # show vlan configuration show vlan config #Add Interface to vlan in Tagged (Trunk) mode: config vlan member add <vlan_value1> Ethernet<interface1> config vlan member add <vlan_value2> Ethernet<interface2> # Inter-VLAN routing # Configure IP addresses on VLAN1 and VLAN2 # Syntax config interface ip add Vlan<number1> <IP_ADDRESS1> config interface ip add Vlan<number2> <IP_ADDRESS2> # Example config interface ip add Vlan1 192.168.1.2/24 config interface ip add Vlan2 192.168.2.1/24 # Validate Ip Interface show ip interface # Verify the Subinterface and VLAN status show vlan brief |
| DHCP Relay | |
|
# DHCP Relay Command #Enable IP routing function when using DHCP relay. set ip routing enable <true | false> # Enable the DHCP relay function on the L3 VLAN interface connected to the client. set protocols dhcp relay interface <vlan-interface-name> disable <true | false> # Configure the IP address of the DHCP server. set protocols dhcp relay interface<vlan-interface-name> dhcp-server-address <ipv4-address> # Configure the IP address of the DHCP relay agent. set protocols dhcp relay interface <vlan-interface-name> relay-agent-address <agent-ipv4-address> |
# SONiC Command to enable DHCP relay config feature state dhcp_relay enabled # Enable DHCP relay on Vlan number config vlan dhcp_relay add <vlan_number> <IP_ADDRESS> #Enable DHCP relay on Loopback interface config vlan dhcp_relay src_intf add <vlan_number> Loopback0 #Example config vlan dhcp_relay add 10 192.168.20.100 config vlan dhcp_relay src_intf add 10 Loopback0 |
BGP Routing
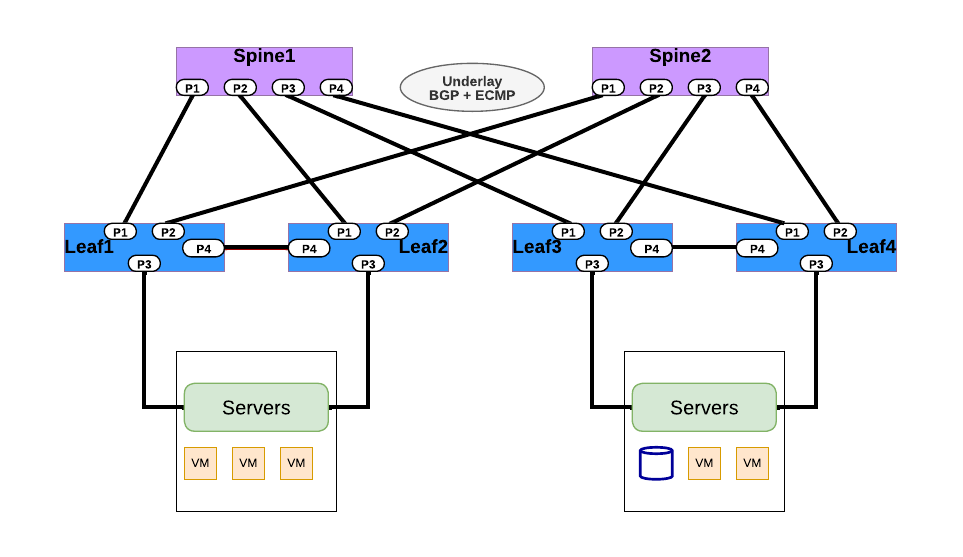
| PICOS | SONiC |
|---|---|
| BGP Routing | |
|
#Command to configure BGP routing - set protocols bgp router-id <System_loopback_IP> set protocols bgp local-as <LOCAL_AS_NUMBER> set protocols bgp local-as <LOCAL_AS_NUMBER> set protocols bgp neighbor <Neighbor_IP> remote-as <REMOTE_AS_NUMBER> set protocols bgp local-as <LOCAL_AS_NUMBER> set protocols bgp neighbor <Neighbor_IP> remote-as <REMOTE_AS_NUMBER> set protocols bgp peer-group <LEAF_NAME> set protocols bgp neighbor <LEAF_NAME> remote-as external set protocols bgp neighbor <Neighbor_IP> peer-group <LEAF_NAME> set protocols bgp neighbor <Neighbor_IP> peer-group <LEAF_NAME> Commit #Example BGP routing configuration set protocols bgp router-id 1.1.1.1 set protocols bgp local-as 100 set protocols bgp local-as 100 set protocols bgp neighbor 192.168.49.1 remote-as 200 set protocols bgp local-as 100 set protocols bgp neighbor 192.168.49.1 remote-as 100 set protocols bgp peer-group Leaf1 set protocols bgp neighbor leaf1 remote-as external set protocols bgp neighbor 10.10.0.1 peer-group Leaf1 set protocols bgp neighbor 10.10.0.12 peer-group Leaf1 commit #Command to show BGP routes summary run show bgp route <ip> |
#vtysh sonic command to configure BGP routing - router bgp <ASN_NUMBER> bgp router-id <System_loopback_IP> no bgp ebgp-requires-policy bgp bestpath as-path multipath-relax neighbor FABRIC peer-group neighbor FABRIC capability extended-nexthop neighbor <Neighbor_IP> remote-as <REMOTE_ASN_NUMBER> neighbor <Neighbor_IP> peer-group FABRIC #Example BGP routing configuration router bgp 65001 bgp router-id 10.0.2.1 no bgp ebgp-requires-policy bgp bestpath as-path multipath-relax neighbor FABRIC peer-group neighbor FABRIC capability extended-nexthop neighbor 172.16.10.0 remote-as 2001 neighbor 172.16.10.0 peer-group FABRIC neighbor 172.16.10.8 remote-as 2002 neighbor 172.16.10.8 peer-group FABRIC neighbor 192.168.3.1 remote-as 2003 neighbor 192.168.3.1 peer-group FABRIC #Command to show BGP routes summary show ip bgp summary show ip bgp neighbors show ip bgp network show ipv6 bgp summary show ipv6 bgp neighbors show ipv6 bgp network |
OSPF Routing
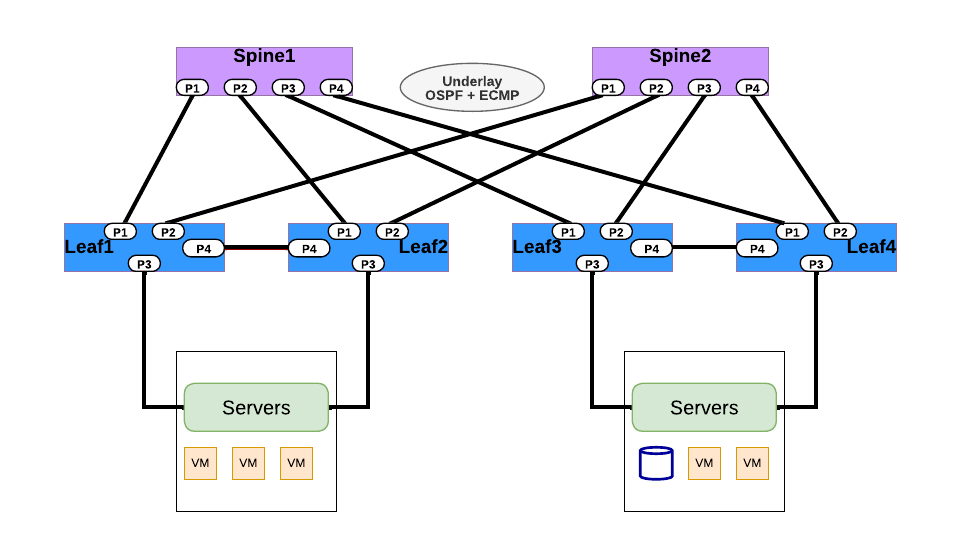
| PICOS | SONiC |
|---|---|
| OSPF Routing | |
|
#Configure OSPF routing set protocols ospf router-id <Router_ID> set protocols ospf area <area-id> area-type set protocols ospf area <Aread_ID> set protocols ospf area <Aread_ID> area-type stub set protocols ospf area <Aread_ID> area-type nssa set protocol ospf interface <vlan-interface> area {<ipv4>|<0-4294967295>} set vlans vlan-id <vlan-id> l3-interface "vlan-number" set interface gigabit-ethernet ge-x/y/z family ethernet-switching native-vlan-id <vlan-id> set interface gigabit-ethernet ge-x/y/z family ethernet-switching native-vlan-id <vlan-id> set l3-interface vlan-interface vlan<number> address <IPV4_Address> prefix-length <Subnet> set l3-interface vlan-interface vlan<number> address <IPV4_Address> prefix-length <Subnet> set protocols ospf interface vlan-<number> area <aread_id> # Example Configuration - OSPF Routing set protocols ospf router-id 1.1.1.1 set protocols ospf area <area-id> area-type set protocols ospf area 0.0.0.0 set protocols ospf area 1.1.1.1 area-type stub set protocols ospf area 2.2.2.2 area-type nssa set protocol ospf interface <vlan-interface> area {<ipv4>|<0-4294967295>} set vlans vlan-id 20 l3-interface "vlan-20" set vlans vlan-id 30 l3-interface "vlan-30" set interface gigabit-ethernet ge-1/1/1 family ethernet-switching native-vlan-id 20 set interface gigabit-ethernet ge-1/1/2 family ethernet-switching native-vlan-id 30 set l3-interface vlan-interface vlan20 address 10.10.70.10 prefix-length 24 set l3-interface vlan-interface vlan30 address 10.10.71.10 prefix-length 24 set protocols ospf interface vlan-20 area 0.0.0.0 set protocols ospf interface vlan-30 area 0.0.0.0 |
#Configure OSPF routing #Syntax router ospf ospf router-id <router-id> network <Network_address> area <Area_number> network <Network_address1> area <Area_number1> network <Network_address2> area <Area_number2> #Command to set OSPF time intervals interface Ethernet<interface> ip ospf hello-interval <hello-interval-time-secs> ip ospf dead-interval <dead-interval-time-secs> router ospf area <aread_number> authentication # Command to set OSPF authentication key interface Ethernet<interface> ip ospf authentication ip ospf authentication-key <key> # Command to set OSPF MD5 Authentication router ospf area 0 authentication message-digest interface Ethernet<interface> ip ospf message-digest-key <key> md5 <key> # Command to configure OSPF Virtual links router ospf area <area_number> virtual-link <System_loopback> # Command to verify OSPF ip routes learned show ip route # Configuration OSPF Routing # Example router ospf ospf router-id 1.1.1.1 network 10.0.0.0/31 area 0 network 192.168.10.0/24 area 0 network 192.168.20.0/24 area 0 network 192.168.30.0/24 area 0 #Enable OSPF hello timers under interface #Example interface Ethernet56 ip ospf hello-interval 20 ip ospf dead-interval 20 # Enable OSPF Authentication globally #Example router ospf area 0 authentication # Enable OSPF Authentication over interface #Example interface Ethernet56 ip ospf authentication ip ospf authentication-key 123 #Enable OSPF MD5 Key #Example router ospf area 0 authentication message-digest interface Ethernet56 ip ospf message-digest-key 1 md5 123 #Verify Ip routing Table #Example show ip route #Configure OSPF virtual links #Example router ospf area 1 virtual-link 3.3.3.3 router ospf area 1 virtual-link 2.2.2.2 |
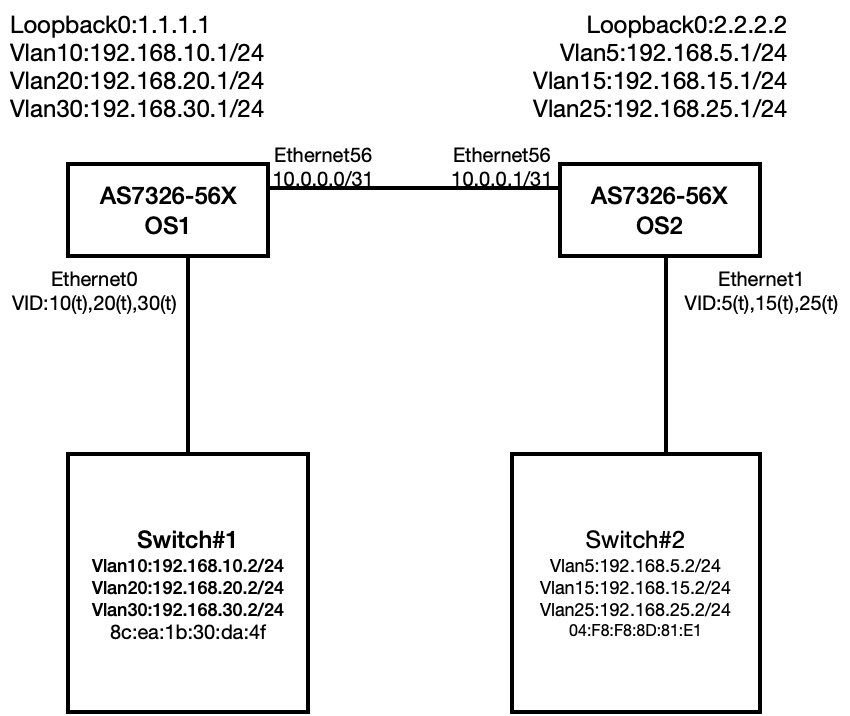
AS7326-56X-OS1 Configuration VLAN and IP Configuration
config interface ip add Loopback0 1.1.1.1/32
config vlan member add 10 Ethernet0
config vlan member add 20 Ethernet0
config vlan member add 30 Ethernet0
config interface ip add Ethernet0.10 192.168.10.1/24
config interface ip add Ethernet0.20 192.168.20.1/24
config interface ip add Ethernet0.30 192.168.30.1/24
config interface ip add Ethernet56 10.0.0.0/31
OSPF Configuration
admin@sonic:~$ vtysh
sonic(config)# router ospf
sonic(config-router)# network 10.0.0.0/31 area 0
sonic(config-router)# network 192.168.10.0/24 area 0
sonic(config-router)# network 192.168.20.0/24 area 0
sonic(config-router)# network 192.168.30.0/24 area 0
OSPF Routing Verification Command
sonic# show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface RXmtL RqstL DBsmL
192.168.25.1 1 Full/DR 31.440s 10.0.0.1 Ethernet56:10.0.0.0 0 0 0
sonic# show ip route
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
K>* 0.0.0.0/0 [0/202] via 188.188.1.1, eth0, 00:07:45
C>* 1.1.1.1/32 is directly connected, Loopback0, 00:07:25
O 10.0.0.0/31 [110/10] is directly connected, Ethernet56, 00:06:42
C>* 10.0.0.0/31 is directly connected, Ethernet56, 00:07:25
C>* 188.188.0.0/16 is directly connected, eth0, 00:07:46
O>* 192.168.5.0/24 [110/20] via 10.0.0.1, Ethernet56, 00:06:32
O 192.168.10.0/24 [110/10] is directly connected, Vlan10, 00:04:54
C>* 192.168.10.0/24 is directly connected, Vlan10, 00:07:24
O>* 192.168.15.0/24 [110/20] via 10.0.0.1, Ethernet56, 00:06:32
O 192.168.20.0/24 [110/10] is directly connected, Vlan20, 00:04:50
C>* 192.168.20.0/24 is directly connected, Vlan20, 00:07:24
O>* 192.168.25.0/24 [110/20] via 10.0.0.1, Ethernet56, 00:06:32
O 192.168.30.0/24 [110/10] is directly connected, Vlan30, 00:04:47
C>* 192.168.30.0/24 is directly connected, Vlan30, 00:07:24
AS7326-56X-OS2 Configuration VLAN and IP Configuration
config interface ip add Loopback0 2.2.2.2/32
config vlan member add 5 Ethernet0
config vlan member add 15 Ethernet0
config vlan member add 25 Ethernet0
config interface ip add Ethernet0.5 192.168.51/24
config interface ip add Ethernet0.15 192.168.15.1/24
config interface ip add Ethernet0.25 192.168.25.1/24
config interface ip add Ethernet56 10.0.0.1/31
OSPF Configuration
admin@sonic:~$ vtysh
sonic(config)# router ospf
sonic(config-router)# network 10.0.0.0/31 area 0
sonic(config-router)# network 192.168.5.0/24 area 0
sonic(config-router)# network 192.168.15.0/24 area 0
sonic(config-router)# network 192.168.25.0/24 area 0
OSPF Routing Verification Command OS2:
sonic# show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface RXmtL RqstL DBsmL
188.188.98.39 1 Full/Backup 33.721s 10.0.0.0 Ethernet56:10.0.0.1 0 0 0
sonic# show ip route
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
K>* 0.0.0.0/0 [0/202] via 188.188.1.1, eth0, 02:15:38
C>* 2.2.2.2/32 is directly connected, Loopback0, 02:15:18
O 10.0.0.0/31 [110/10] is directly connected, Ethernet56, 00:08:47
C>* 10.0.0.0/31 is directly connected, Ethernet56, 00:08:47
C>* 188.188.0.0/16 is directly connected, eth0, 02:15:39
O 192.168.5.0/24 [110/10] is directly connected, Vlan5, 00:35:34
C>* 192.168.5.0/24 is directly connected, Vlan5, 00:35:34
O>* 192.168.10.0/24 [110/20] via 10.0.0.0, Ethernet56, 00:06:14
O 192.168.15.0/24 [110/10] is directly connected, Vlan15, 00:35:34
C>* 192.168.15.0/24 is directly connected, Vlan15, 00:35:34
O>* 192.168.20.0/24 [110/20] via 10.0.0.0, Ethernet56, 00:06:10
O 192.168.25.0/24 [110/10] is directly connected, Vlan25, 00:35:34
C>* 192.168.25.0/24 is directly connected, Vlan25, 00:35:34
O>* 192.168.30.0/24 [110/20] via 10.0.0.0, Ethernet56, 00:06:07
VRF Routing
| PICOS | SONiC |
|---|---|
|
# Command to configure VRRP set ip routing enable true set ip vrf vrf1 description east set ip vrf vrf2 description east # Command to bind the Layer 3 VLAN interface to the VRF. set vlan-interface interface vlan<vlan-id> vrf <VRF-ID> # Command to add static route entry into the VRF. set protocols static vrf <VRF-ID> route <IPV4_address> next-hop <IPV4_address> set protocols static vrf <VRF-ID> route <IPV6_address> next-hop <IPV6_address # Command to validate show VRF instance created run show vrf |
# SONiC command to create a VRF- #Syntax config vrf add config vrf add <vrf-name> config vrf del <vrf-name> config vrf add_vrf_vni_map <vrf-name> # Command to bind Layer 3 VLAN interface to the VRF. config vrf add <VRF-ID> config vxlan add vtep <VTEP_ENDPOINT_IP> config vxlan evpn_nvo add evpnnvo vtep config vrf add_vrf_vni_map <VRF-ID> <VNI_VALUE> # Command to unbind the Layer 3 VLAN interface to the VRF # Syntax config vrf del_vrf_vni_map <vrf-name> # Command to configure a static route entry into the VRF # Example ip route <A.B.C.D/M> <A.B.C.D> nexthop-vrf <vrf-name> # Command to import VRF table into default routing table import vrf default #Command to add bgp routing entry with VRF and import route leaking policy into VRF routing table router bgp <AS_NUMBER> vrf address-family ipv4 unicast router bgp <AS_NUMBER> vrf address-family ipv4 unicast |
Create VRF instance
admin@sonic:~$ config vrf add Vrf_01
admin@sonic:~$ config interface vrf bind Ethernet0 Vrf_01
Checking the VRF
admin@sonic:~$ show vrf
VRF Interfaces
------ ------------
Vrf_01 Ethernet0
admin@sonic:~$ show ip interfaces
Interface Master IPv4 address/mask Admin/Oper BGP Neighbor Neighbor IP
----------- -------- ------------------- ------------ -------------- -------------
Ethernet0 Vrf_01 192.168.1.1/24 up/up N/A N/A
Loopback0 10.1.0.1/32 up/up N/A N/A
docker0 240.127.1.1/24 up/down N/A N/A
eth0 188.188.97.31/16 up/up N/A N/A
lo 127.0.0.1/8 up/up N/A N/A
Checking the routing table.
admin@sonic:~$ show ip route vrf Vrf_01
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
VRF Vrf_01:
C>* 192.168.1.0/24 is directly connected, Ethernet0, 00:02:37
admin@sonic:~$ show ip route vrf all
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
VRF Vrf_01:
C>* 192.168.1.0/24 is directly connected, Ethernet0, 00:00:31
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
K>* 0.0.0.0/0 [0/202] via 188.188.1.1, eth0, 00:15:16
C>* 10.1.0.1/32 is directly connected, Loopback0, 00:15:16
C>* 188.188.0.0/16 is directly connected, eth0, 00:15:16
Management VRF Create Management VRF
admin@sonic:~$ config vrf add mgmt
Checking the Management VRF
admin@sonic:~$ show mgmt-vrf
ManagementVRF : Enabled
Management VRF interfaces in Linux:
128: mgmt: <NOARP,MASTER,UP,LOWER_UP> mtu 65536 qdisc noqueue state UP mode DEFAULT group default qlen 1000
link/ether 52:2f:cc:b8:28:b5 brd ff:ff:ff:ff:ff:ff promiscuity 0 minmtu 68 maxmtu 1500
vrf table 5000 addrgenmode eui64 numtxqueues 1 numrxqueues 1 gso_max_size 65536 gso_max_segs 65535
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master mgmt state UP mode DEFAULT group default qlen 1000
link/ether 80:a2:35:4f:4f:40 brd ff:ff:ff:ff:ff:ff
129: lo-m: <BROADCAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc noqueue master mgmt state UNKNOWN mode DEFAULT group default qlen 1000
link/ether 0a:25:2e:1f:32:90 brd ff:ff:ff:ff:ff:ff
admin@sonic:~$ show ip interfaces
Interface Master IPv4 address/mask Admin/Oper BGP Neighbor Neighbor IP
----------- -------- ------------------- ------------ -------------- -------------
Ethernet0 Vrf_01 192.168.1.1/24 up/up N/A N/A
Loopback0 10.1.0.1/32 up/up N/A N/A
docker0 240.127.1.1/24 up/down N/A N/A
eth0 mgmt 188.188.97.31/16 up/up N/A N/A
lo 127.0.0.1/8 up/up N/A N/A
lo-m mgmt 127.0.0.1/8 up/up N/A N/A
admin@sonic:~$ show ip route vrf mgmt
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
VRF mgmt:
K>* 0.0.0.0/0 [0/0] via 188.188.1.1, eth0, 00:12:12
C>* 188.188.0.0/16 is directly connected, eth0, 00:12:12
admin@sonic:~$ show ip route vrf all
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
VRF Vrf_01:
C>* 192.168.1.0/24 is directly connected, Ethernet0, 00:01:04
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
C>* 10.1.0.1/32 is directly connected, Loopback0, 00:01:05
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
VRF mgmt:
K>* 0.0.0.0/0 [0/0] via 188.188.1.1, eth0, 00:01:21
C>* 188.188.0.0/16 is directly connected, eth0, 00:01:21
L2-VXLAN Asymmetric IRB Configuration
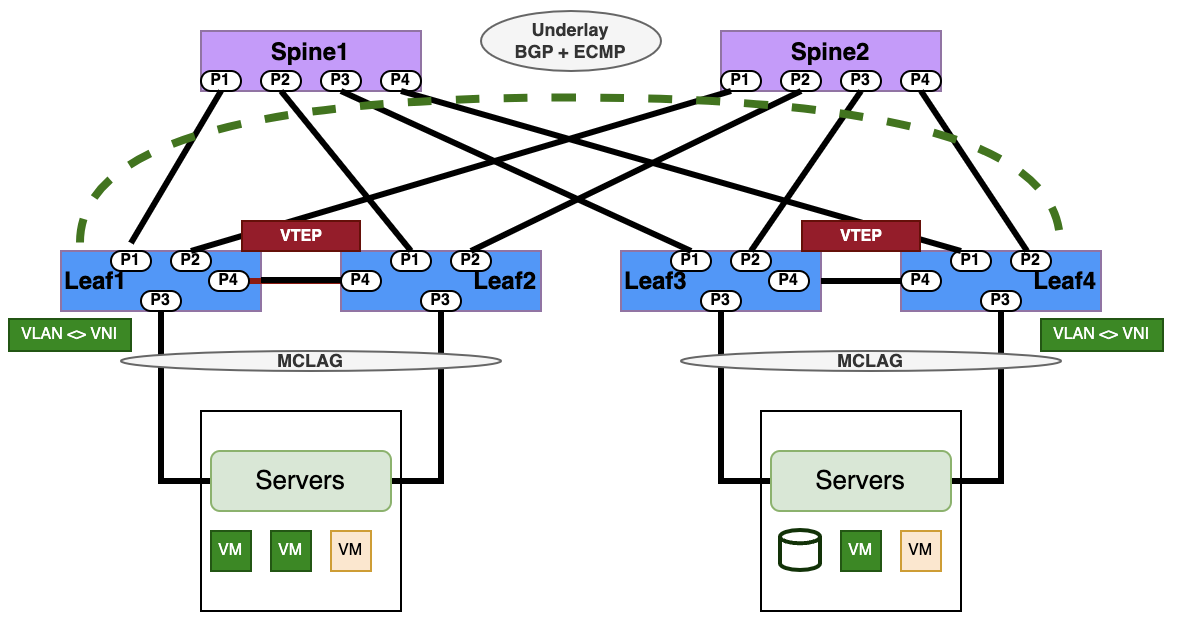
| PICOS | SONiC |
|---|---|
|
# Configure VLAN ID, L3 VLAN interfaces loopback interfaces and IP addressing. #Syntax set vlans vlan-id <VLAN-ID> set ip routing enable true set ip vrf <VRF_NAME> set interface gigabit-ethernet ge-x/y/z family ethernet-switching native-vlan-id <vlan-id1> set interface gigabit-ethernet ge-a/b/c family ethernet-switching native-vlan-id <vlan-id2> set l3-interface loopback lo address <System_loopback_1> prefix-length 32 set l3-interface loopback <VRF_NAME> address <System_loopback_2> prefix-length 32 set l3-interface vlan-interface vlan<vlan_number> address <IP_address> prefix-length <subnet_length> # Configure VXLAN VNI and map VNI IDs to VLAN IDs. set vlans vlan-id <VLAN-ID> l3-interface "vlan<VLAN_NUMBER>" set vxlans source-interface lo address <SYSTEM_LOOPBACK> set vxlans vni <VNI_VALUE> vlan <VLAN-ID> # Configure BGP related configuration set protocols bgp local-as <LOCAL_AS_NUMBER> set protocols bgp router-id <SYSTEM_LOOPBACK> set protocols bgp neighbor <BGP_NEIGHBOR_IP> remote-as "internal" set protocols bgp neighbor <BGP_NEIGHBOR_IP> update-source "<SYSTEM_LOOPBACK>" set protocols bgp neighbor <BGP_NEIGHBOR_IP> evpn activate true set protocols bgp evpn advertise-all-vni set protocols bgp evpn advertise ipv4-unicast set protocols bgp local-as <LOCAL_AS_NUMBER> set protocols bgp router-id <SYSTEM_LOOPBACK> set protocols bgp evpn advertise ipv4-unicast #Verify Configuration- routes and VXLAN tunnels run show route run show bgp route run show vxlan evpn route run show vxlan tunnel #Advertise BGP EVPN Routes set protocols bgp evpn advertise-all-vni set vxlans source-interface loopback address <SYSTEM_LOOPBACK> set vxlans vni <VNI_VALUE> encapsulation vlan <VLAN-ID> #Command to show VXLAN traffic stats run show vxlan statistics |
# Configure LoopBack, VLAN IDs , Ip addressing # Syntax config vlan add <VLAN-ID> config vlan member add <VLAN-ID> Ethernet<interface1> config interface ip add Loopback0 <SYSTEM_LOOPBACK> # Configure BGP routing router bgp <LOCAL_AS_NUMBER> bgp router-id <SYSTEM_LOOPBACK> neighbor <ebgp_neighbor_ip> remote-as <REMOTE_AS_NUMBER> address-family ipv4 network <Network_prefix_advertised> #Configure VXLAN VNI and map VNI IDs to VLAN IDs config vxlan add vtep <SOURCE_VTEP_IP> config vxlan evpn_nvo add nvo vtep config vxlan map add vtep <VLAN-ID> <VNI_VALUE> config vxlan add vtep <DEST_VTEP_IP> config vxlan evpn_nvo add nvo vtep config vxlan map add vtep <VLAN-ID> <VNI_VALUE> #Advertise L2 EVPN Routes router bgp <LOCAL_AS_NUMBER> address-family l2vpn evpn neighbor <ebgp_neighbor_ip> activate Advertise-all-vni #Show VXLAN tunnels , interfaces show ip route show vxlan interface show vxlan vlanvnimap show vxlan tunnel show vxlan remotevtep show evpn vni detail |
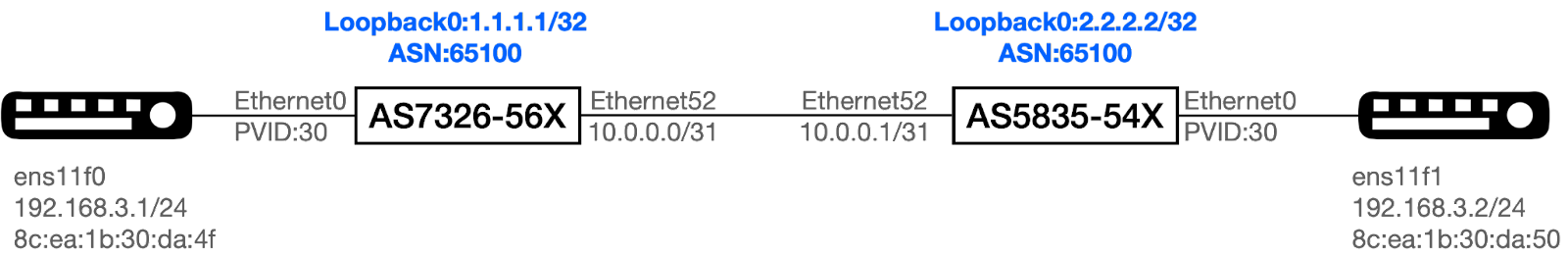
Step 1: Configure IP address to Loopback0 of both switches. AS7326-56X
admin@AS7326-56X:~$ config interface ip remove Loopback0 10.1.0.1/32
admin@AS7326-56X:~$ config interface ip add Loopback0 1.1.1.1/32
AS5835-54X:
admin@AS5835-54X:~$ config interface ip remove Loopback0 10.1.0.1/32
admin@AS5835-54X:~$ config interface ip add Loopback0 2.2.2.2/32
Step 2: Establish BGP Session between Ethernet52 and announce the network. AS7326-56X:
admin@AS7326-56X:~$ vtysh
Hello, this is FRRouting (version 7.2.1-sonic).
Copyright 1996-2005 Kunihiro Ishiguro, et al.
AS7326-56X# configure terminal
AS7326-56X(config)# router bgp 65100
AS7326-56X(config-router)# bgp router-id 1.1.1.1
AS7326-56X(config-router)# neighbor 10.0.0.1 remote-as 65100
AS7326-56X(config-router)# address-family ipv4
AS7326-56X(config-router-af)# network 1.1.1.1/32
AS7326-56X(config-router-af)# end
AS7326-56X# exit
AS5835-54X:
admin@AS5835-54X:~$ vtysh
Hello, this is FRRouting (version 7.2.1-sonic).
Copyright 1996-2005 Kunihiro Ishiguro, et al.
AS5835-54X# configure terminal
AS5835-54X(config)# router bgp 65100
AS5835-54X(config-router)# bgp router-id 2.2.2.2
AS5835-54X(config-router)# neighbor 10.0.0.0 remote-as 65100
AS5835-54X(config-router)# address-family ipv4
AS5835-54X(config-router-af)# network 2.2.2.2/32
AS5835-54X(config-router-af)# end
AS5835-54X# exit
Step 3. Create Vxlan AS7326-56X:
admin@AS7326-56X:~$ config vxlan add vtep 1.1.1.1
admin@AS7326-56X:~$ config vxlan evpn_nvo add nvo vtep
admin@AS7326-56X:~$ config vxlan map add vtep 30 3000
AS5835-54X:
admin@AS5835-54X:~$ config vxlan add vtep 2.2.2.2
admin@AS5835-54X:~$ config vxlan evpn_nvo add nvo vtep
admin@AS5835-54X:~$ config vxlan map add vtep 30 3000
Note :
VNI (VxLAN Network Identifier) : virtual extension of VLAN over IP network.
VTEP (VXLAN Tunnel End Point) : an entity that originates and/or terminates VXLAN tunnels which is specified by a source IP address.
Only one VTEP is allowed on one device. Please use loopback IP address for VTEP's IP address.
NVO (Network Virtualization Overlay)
Only one NVO is allowed on one device.
VNI (VxLAN Network Identifier) : virtual extension of VLAN over IP network.
Step 4: Advertise L2VPN EVPN routes. AS7326-56X:
admin@AS7326-56X:~$ vtysh
Hello, this is FRRouting (version 7.2.1-sonic).
Copyright 1996-2005 Kunihiro Ishiguro, et al.
AS7326-56X#
AS7326-56X# configure terminal
AS7326-56X(config)# router bgp 65100
AS7326-56X(config-router)# address-family l2vpn evpn
AS7326-56X(config-router-af)# neighbor 10.0.0.1 activate
AS7326-56X(config-router-af)# advertise-all-vni
admin@AS5835-54X:~$ vtysh
Hello, this is FRRouting (version 7.2.1-sonic).
AS5835-54X#
AS5835-54X# configure terminal
AS5835-54X(config)# router bgp 65100
AS5835-54X(config-router)# address-family l2vpn evpn
AS5835-54X(config-router-af)# neighbor 10.0.0.0 activate
AS5835-54X(config-router-af)# advertise-all-vni
Check VxLAN interface configuration.AS7326-56X:
admin@AS7326-56X:~$ show vxlan interface
VTEP Information:
VTEP Name : vtep, SIP : 1.1.1.1
Source interface : Loopback0
AS5835-54X:
admin@AS5835-54X:~$ show vxlan interface
VTEP Information:
VTEP Name : vtep, SIP : 2.2.2.2
Source interface : Loopback0
Check vxlan and VLAN mapping.AS7326-56X:
admin@AS7326-56X:~$ show vxlan vlanvnimap
+--------+-------+
| VLAN | VNI |
+========+=======+
| Vlan30 | 3000 |
+--------+-------+
Total count : 1
AS5835-54X:
admin@AS5835-54X:~$ show vxlan vlanvnimap
+--------+-------+
| VLAN | VNI |
+========+=======+
| Vlan30 | 3000 |
+--------+-------+
Total count : 1
Check the status for Vxlan tunneling. AS7326-56X:(202111.3)
admin@AS7326-56X:~$ show vxlan tunnel
vxlan tunnel name source ip destination ip tunnel map name tunnel map mapping(vni -> vlan)
------------------- ----------- ---------------- ----------------- ---------------------------------
vtep 1.1.1.1 map_3000_Vlan30 3000 -> Vlan30
Total count : 1
AS7326-56X:(202111.3)
admin@AS7326-56X:~$ show vxlan remotevtep
+---------+---------+-------------------+--------------+
| SIP | DIP | Creation Source | OperStatus |
+=========+=========+===================+==============+
| 1.1.1.1 | 2.2.2.2 | EVPN | oper_up |
+---------+---------+-------------------+--------------+
Total count : 1
AS5835-54X:(202111.3)
admin@AS5835-54X:~$ show vxlan tunnel
vxlan tunnel name source ip destination ip tunnel map name tunnel map mapping(vni -> vlan)
------------------- ----------- ---------------- ----------------- ---------------------------------
vtep 2.2.2.2 map_3000_Vlan30 3000 -> Vlan30
Total count : 1
AS5835-54X:(202111.3)
admin@AS5835-54X:~$ show vxlan remotevtep
| SIP | DIP | Creation Source | OperStatus |
+=========+=========+===================+==============+
| 2.2.2.2 | 1.1.1.1 | EVPN | oper_up |
+---------+---------+-------------------+--------------+
Total count : 1
Check the Mac learning. AS7326-56X:(202111.3)
admin@AS7326-56X:~$ show mac
No. Vlan MacAddress Port Type
----- ------ ----------------- ------------------ -------
1 30 8C:EA:1B:30:DA:50 VxLAN DIP: 2.2.2.2 Static
2 30 8C:EA:1B:30:DA:4F Ethernet0 Dynamic
Total number of entries 2
AS7326-56X(202111.3)
admin@AS7326-56X:~$ show mac
No. Vlan MacAddress Port Type
----- ------ ----------------- --------- -------
1 30 8C:EA:1B:30:DA:4F Ethernet0 Dynamic
Total number of entries 1
admin@AS7326-56X:~$ show vxlan remotemac all
+--------+-------------------+--------------+-------+-------+---------+
| VLAN | MAC | RemoteVTEP | ESI | VNI | Type |
+========+===================+==============+=======+=======+=========+
| Vlan30 | 8c:ea:1b:30:da:50 | 2.2.2.2 | | 3000 | dynamic |
+--------+-------------------+--------------+-------+-------+---------+
Total count : 1
Note.
"8C:EA:1B:30:DA:50" is synced from remote vtep(2.2.2.2).
"8C:EA:1B:30:DA:4F" is learned locally.
AS5835-54X:(202111.3)
admin@AS5835-54X:~$ show mac
No. Vlan MacAddress Port Type
----- ------ ----------------- ------------------ -------
1 30 8C:EA:1B:30:DA:50 Ethernet0 Dynamic
2 30 8C:EA:1B:30:DA:4F VxLAN DIP: 1.1.1.1 Static
Total number of entries 2
AS5835-54X:(202111.3)
admin@AS5835-54X:~$ show mac
No. Vlan MacAddress Port Type
----- ------ ----------------- --------- -------
1 30 8C:EA:1B:30:DA:50 Ethernet0 Dynamic
Total number of entries 1
admin@AS5835-54X:~$ show vxlan remotemac all
+--------+-------------------+--------------+-------+-------+---------+
| VLAN | MAC | RemoteVTEP | ESI | VNI | Type |
+========+===================+==============+=======+=======+=========+
| Vlan30 | 8c:ea:1b:30:da:4f | 1.1.1.1 | | 3000 | dynamic |
+--------+-------------------+--------------+-------+-------+---------+
Total count : 1
Check IPv4 BGP session AS7326-56X:
AS7326-56X# show bgp ipv4 summary
IPv4 Unicast Summary:
BGP router identifier 1.1.1.1, local AS number 65100 vrf-id 0
BGP table version 6
RIB entries 3, using 552 bytes of memory
Peers 1, using 20 KiB of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.0.0.1 4 65100 80 85 0 0 0 01:01:28 1
Total number of neighbors 1
AS5835-54X:
AS5835-54X# show bgp ipv4 summary
IPv4 Unicast Summary:
BGP router identifier 2.2.2.2, local AS number 65100 vrf-id 0
BGP table version 6
RIB entries 3, using 552 bytes of memory
Peers 1, using 20 KiB of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.0.0.0 4 65100 79 79 0 0 0 01:01:28 1
Total number of neighbors 1
Check L2EVPN BGP session AS7326-56X:
AS7326-56X# show bgp l2vpn evpn summary
BGP router identifier 1.1.1.1, local AS number 65100 vrf-id 0
BGP table version 0
RIB entries 3, using 552 bytes of memory
Peers 1, using 20 KiB of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.0.0.1 4 65100 82 87 0 0 0 01:03:43 3
Total number of neighbors 1
AS5835-54X:
AS5835-54X# show bgp l2vpn evpn summary
BGP router identifier 2.2.2.2, local AS number 65100 vrf-id 0
BGP table version 0
RIB entries 3, using 552 bytes of memory
Peers 1, using 20 KiB of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
10.0.0.0 4 65100 81 81 0 0 0 01:03:43 3
Total number of neighbors 1
Check underlay routing AS7326-56X:
AS7326-56X# show ip route
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
K>* 0.0.0.0/0 [0/202] via 188.188.1.1, eth0, 00:49:45
C>* 1.1.1.1/32 is directly connected, Loopback0, 00:49:14
B>* 2.2.2.2/32 [200/0] via 10.0.0.1, Ethernet52, 00:42:04
C>* 10.0.0.0/31 is directly connected, Ethernet52, 00:49:13
C>* 188.188.0.0/16 is directly connected, eth0, 00:49:45
AS5835-54X:
AS5835-54X# show ip route
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, D - SHARP,
F - PBR, f - OpenFabric,
> - selected route, * - FIB route, q - queued route, r - rejected route
K>* 0.0.0.0/0 [0/0] via 188.188.1.1, eth0, 00:49:57
B>* 1.1.1.1/32 [200/0] via 10.0.0.0, Ethernet52, 00:42:25
C>* 2.2.2.2/32 is directly connected, Loopback0, 00:46:34
C>* 10.0.0.0/31 is directly connected, Ethernet52, 00:46:33
C>* 188.188.0.0/16 is directly connected, eth0, 00:49:57
Check Vxlan VNI status AS7326-56X:
AS7326-56X# show evpn vni detail
VNI: 3000
Type: L2
Tenant VRF: default
VxLAN interface: vtep-30
VxLAN ifIndex: 68
Local VTEP IP: 1.1.1.1
Mcast group: 0.0.0.0
Remote VTEPs for this VNI:
2.2.2.2 flood: HER
Number of MACs (local and remote) known for this VNI: 3
Number of ARPs (IPv4 and IPv6, local and remote) known for this VNI: 3
Advertise-gw-macip: No
AS5835-54X:
AS5835-54X# show evpn vni detail
VNI: 3000
Type: L2
Tenant VRF: default
VxLAN interface: vtep-30
VxLAN ifIndex: 66
Local VTEP IP: 2.2.2.2
Mcast group: 0.0.0.0
Remote VTEPs for this VNI:
1.1.1.1 flood: HER
Number of MACs (local and remote) known for this VNI: 3
Number of ARPs (IPv4 and IPv6, local and remote) known for this VNI: 3
Advertise-gw-macip: No
Check the evpn mac learning AS7326-56X:
AS7326-56X# show evpn mac vni all
VNI 3000 #MACs (local and remote) 3
MAC Type Intf/Remote VTEP VLAN Seq #'s
8c:ea:1b:30:da:50 remote 2.2.2.2 1/0
8c:ea:1b:30:da:4f local Ethernet0 30 0/0
AS5835-54X:
AS5835-54X# show evpn mac vni all
VNI 3000 #MACs (local and remote) 3MAC Type Intf/Remote VTEP VLAN Seq #'s
8c:ea:1b:30:da:50 local Ethernet0 30 0/0
8c:ea:1b:30:da:4f remote 1.1.1.1 1/0
Check the type 2 EVPN route AS7326-56X:
AS7326-56X# show bgp l2vpn evpn route type macip
BGP table version is 2, local router ID is 1.1.1.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
EVPN type-1 prefix: [1]:[EthTag]:[ESI]:[IPlen]:[VTEP-IP]
EVPN type-2 prefix: [2]:[EthTag]:[MAClen]:[MAC]:[IPlen]:[IP]
EVPN type-3 prefix: [3]:[EthTag]:[IPlen]:[OrigIP]
EVPN type-4 prefix: [4]:[ESI]:[IPlen]:[OrigIP]
EVPN type-5 prefix: [5]:[EthTag]:[IPlen]:[IP]
Network Next Hop Metric LocPrf Weight Path
Extended Community
Route Distinguisher: 1.1.1.1:2
*> [2]:[0]:[48]:[8c:ea:1b:cc:10:a4]
1.1.1.1 32768 i
ET:8 RT:65100:3000
Route Distinguisher: 2.2.2.2:2
*>i[2]:[0]:[48]:[80:a2:35:5a:22:50]
2.2.2.2 100 0 i
RT:65100:3000 ET:8
Displayed 2 prefixes (2 paths) (of requested type)
AS5835-54X:
AS5835-54X# show bgp l2vpn evpn route type macip
BGP table version is 2, local router ID is 2.2.2.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
EVPN type-1 prefix: [1]:[EthTag]:[ESI]:[IPlen]:[VTEP-IP]
EVPN type-2 prefix: [2]:[EthTag]:[MAClen]:[MAC]:[IPlen]:[IP]
EVPN type-3 prefix: [3]:[EthTag]:[IPlen]:[OrigIP]
EVPN type-4 prefix: [4]:[ESI]:[IPlen]:[OrigIP]
EVPN type-5 prefix: [5]:[EthTag]:[IPlen]:[IP]
Network Next Hop Metric LocPrf Weight Path
Extended Community
Route Distinguisher: 1.1.1.1:2
*>i[2]:[0]:[48]:[8c:ea:1b:cc:10:a4]
1.1.1.1 100 0 i
RT:65100:3000 ET:8
Route Distinguisher: 2.2.2.2:2
*> [2]:[0]:[48]:[80:a2:35:5a:22:50]
2.2.2.2 32768 i
ET:8 RT:65100:3000
Displayed 2 prefixes (2 paths) (of requested type)
Check the type 3 EVPN route AS7326-56X:
AS7326-56X# show bgp l2vpn evpn route type multicast
BGP table version is 3, local router ID is 1.1.1.1
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
EVPN type-2 prefix: [2]:[EthTag]:[MAClen]:[MAC]:[IPlen]:[IP]
EVPN type-3 prefix: [3]:[EthTag]:[IPlen]:[OrigIP]
EVPN type-4 prefix: [4]:[ESI]:[IPlen]:[OrigIP]
EVPN type-5 prefix: [5]:[EthTag]:[IPlen]:[IP]
Network Next Hop Metric LocPrf Weight Path
Extended Community
Route Distinguisher: 1.1.1.1:2
*> [3]:[0]:[32]:[1.1.1.1]
1.1.1.1 32768 i
ET:8 RT:65100:3000
Route Distinguisher: 2.2.2.2:2
*>i[3]:[0]:[32]:[2.2.2.2]
2.2.2.2 100 0 i
RT:65100:3000 ET:8
Displayed 2 prefixes (2 paths) (of requested type)
AS5835-54X:
AS5835-54X# show bgp l2vpn evpn route type multicast
BGP table version is 3, local router ID is 2.2.2.2
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
EVPN type-2 prefix: [2]:[EthTag]:[MAClen]:[MAC]:[IPlen]:[IP]
EVPN type-3 prefix: [3]:[EthTag]:[IPlen]:[OrigIP]
EVPN type-4 prefix: [4]:[ESI]:[IPlen]:[OrigIP]
EVPN type-5 prefix: [5]:[EthTag]:[IPlen]:[IP]
Network Next Hop Metric LocPrf Weight Path
Extended Community
Route Distinguisher: 1.1.1.1:2
*>i[3]:[0]:[32]:[1.1.1.1]
1.1.1.1 100 0 i
RT:65100:3000 ET:8
Route Distinguisher: 2.2.2.2:2
*> [3]:[0]:[32]:[2.2.2.2]
2.2.2.2 32768 i
ET:8 RT:65100:3000
L3-VXLAN Symmetric IRB Configuration
| PICOS | SONiC |
|---|---|
|
# Configure physical interfaces, VLAN interfaces and assign VLAN IDs and IP addresses. set interface gigabit-ethernet ge-x/y/z family ethernet-switching native-vlan-id <vlan-id1> set interface gigabit-ethernet ge-x/y/z family ethernet-switching native-vlan-id <vlan-id2> set interface gigabit-ethernet ge-x/y/z family ethernet-switching port-mode "trunk" set interface gigabit-ethernet ge-x/y/z family ethernet-switching vlan members <vlan-id1> set interface gigabit-ethernet ge-x/y/z family ethernet-switching vlan members <vlan-id2> set l3-interface loopback lo address <SYSTEM_LOOPBACK1> prefix-length 32 set l3-interface loopback lo address <SYSTEM_LOOPBACK2> prefix-length 32 set l3-interface loopback lo address <SYSTEM_LOOPBACK_IPV6> prefix-length 128 set l3-interface vlan-interface vlan<VLAN_NUMBER> vrf "VRF_NAME" set l3-interface vlan-interface vlan<VLAN_NUMBER> address <IP_ADDRESS> prefix-length <SUBNET_LENGTH> set l3-interface vlan-interface vlan<VLAN_NUMBER> vrf "VRF_NAME" #Enable IP routing and configure VRF and hostname set ip routing enable true set ip vrf <VRF_NAME> set vxlans vrf <VRF_NAME> l3-vni <VNI_VALUE> prefix-routes-only delete vxlans vrf <VRF_NAME> l3-vni <VNI_VALUE> prefix-routes-only set vxlans vrf vrf1 l3-vni <VNI_VALUE> prefix-routes-only # Enable IP Routing and Configure VRF set ip routing enable true set ip vrf vrf1 #Create an L3 VNI in vrf1. set vxlans source-interface lo address <SYSTEM_LOOPBACK> set vxlans vrf <VRF-NAME> l3-vni <VNI_VALUE> #Advertise all VNI through BGP routing set protocol bgp evpn advertise-all-vni #Enable EVPN Between BGP Peers set protocols bgp local-as <LOCAL_AS_NUMBER> set protocols bgp router-id <SYSTEM_LOOPBACK> set protocols bgp neighbor <ebgp_neighbor_ip> remote-as <REMOTE_AS_NUMBER> set protocols bgp ebgp-requires-policy false set protocols bgp local-as <LOCAL_ASN_NUMBER> set protocols bgp router-id <SYSTEM_LOOPBACK> set protocols bgp neighbor <ebgp_neighbor_ip> remote-as "external" set protocols bgp neighbor <ebgp_neighbor_ip> update-source "<SYSTEM_LOOPBACK>” set protocols bgp neighbor <ebgp_neighbor_ip> evpn activate true set protocols bgp ipv4-unicast network <Prefix_subnet_advertised> # Configure BGP routing and advertise EVPN routes set protocols bgp evpn advertise-all-vni set protocols bgp evpn advertise ipv4-unicast set protocols bgp vrf <VRF_NAME> local-as <LOCAL_AS_NUMBER> set protocols bgp vrf <VRF_NAME> router-id <SYSTEM_LOOPBACK> set protocols bgp vrf <VRF_NAME> ipv4-unicast network <PREFIX_SUBNET_ADVERTISED> set protocols bgp vrf <VRF_NAME> evpn advertise ipv4-unicast |
# Configure physical interfaces, VLAN interfaces and assign VLAN IDs and IP addresses
config interface ip add Loopback0 <SYSTEM_LOOPBACK> #Configure VRF Setting config vrf add <VRF-NAME> config interface vrf bind VLAN<VLAN_NUMBER> <VRF-NAME> config interface ip add VLAN<VLAN_NUMBER> <IP_ADDRESS> #Create VxLAN,map VNI to VLAN config vxlan add vtep <SOURCE_VTEP_IP> config vxlan evpn_nvo add nvo vtep config vxlan map add vtep <VLAN-ID> <VNI_VALUE> config save -y #Configure layer3 VNI and map it to VRF value config vrf add_vrf_vni_map <VRF-NAME> <VNI_VALUE> config save -y #Establish a BGP environment for EVPN # vtysh command router bgp <LOCAL_AS_NUMBER> neighbor <ebgp_neighbor_ip> remote-as <REMOTE_AS_NUMBER> address-family ipv4 unicast network %lt;PREFIX_ADVERTISED> exit address-family l2vpn evpn neighbor <ebgp_neighbor_ip> activate = advertise-all-vni end # Configure VRF and VNI values configure terminal vrf <VRF-NAME> vni <VNI_VALUE> end # Configure BGP routing and advertise EVPN routes router bgp <LOCAL_AS_NUMBER> vrf <VRF-NAME> address-family ipv4 unicast redistribute connected address-family l2vpn evpn advertise ipv4 unicast write # Commands to verify VXLAN tunnels show vxlan interface show vxlan vlanvnimap show vxlan tunnel show vxlan remotevtep #Commands to verify EVPN routes and BGP routes show evpn vni detail show bgp summary show ip route vrf all |

Configure IP address and Loopback IPs of both switches. AS5835-54X
admin@SONIC01:~$ config interface ip add Loopback0 1.1.1.1/32
admin@SONIC01:~$ config interface ip add Ethernet48 10.0.0.4/31
A4630-54PE
admin@SONIC02:~$ config interface ip add Loopback0 2.2.2.2/32
admin@SONIC02:~$ config interface ip add Ethernet52 10.0.0.5/31
Configure VRF Setting AS5835-54X
admin@SONIC01:~$ config vrf add Vrf01
admin@SONIC01:~$ config interface vrf bind Vlan30 Vrf01
admin@SONIC01:~$ config interface vrf bind Vlan10 Vrf01
admin@SONIC01:~$ config interface ip add Vlan10 192.168.1.254/24
A4630-54PE
admin@SONIC02:~$ config vrf add Vrf01
admin@SONIC02:~$ config interface vrf bind Vlan30 Vrf01
admin@SONIC02:~$ config interface vrf bind Vlan20 Vrf01
admin@SONIC02:~$ config interface ip add Vlan20 192.168.2.254/24
Establish BGP Session between Ethernet48 and Ethernet52 AS5835-54X
admin@SONIC01:~$ vtysh
sonic# configure terminal
sonic(config)# router bgp 65100
sonic(config-router)# neighbor 10.0.0.5 remote-as 65100
sonic(config-router)# address-family ipv4 unicast
sonic(config-router-af)# network 1.1.1.1/32
sonic(config-router-af)# exit
sonic(config-router)# address-family l2vpn evpn
sonic(config-router-af)# neighbor 10.0.0.5 activate
sonic(config-router-af)# advertise-all-vni
sonic(config-router-af)# end
sonic# configure terminal
sonic(config)# vrf Vrf01
sonic(config-vrf)# vni 3000
sonic(config-vrf)# end
sonic# configure terminal
sonic(config)# router bgp 65100 vrf Vrf01
sonic(config-router)# address-family ipv4 unicast
sonic(config-router-af)# redistribute connected
sonic(config-router-af)# exit
sonic(config-router)# address-family l2vpn evpn
sonic(config-router-af)# advertise ipv4 unicast
sonic(config-router-af)# end
sonic# write
A4630-54PE
admin@SONIC02:~$ vtysh
sonic# configure terminal
sonic(config)# router bgp 65100
sonic(config-router)# neighbor 10.0.0.4 remote-as 65100
sonic(config-router)# address-family ipv4 unicast
sonic(config-router-af)# network 2.2.2.2/32
sonic(config-router-af)# exit
sonic(config-router)# address-family l2vpn evpn
sonic(config-router-af)# neighbor 10.0.0.4 activate
sonic(config-router-af)# advertise-all-vni
sonic(config-router-af)# end
sonic# configure terminal
sonic(config)# vrf Vrf01
sonic(config-vrf)# vni 3000
sonic(config-vrf)# end
sonic# configure terminal
sonic(config)# router bgp 65100 vrf Vrf01
sonic(config-router)# address-family ipv4 unicast
sonic(config-router-af)# redistribute connected
sonic(config-router-af)# exit
sonic(config-router)# address-family l2vpn evpn
sonic(config-router-af)# advertise ipv4 unicast
sonic(config-router-af)# end
sonic# write
Create Vxlan AS5835-54X configuring VTEP_name (vtep) and its IP address
admin@SONIC01:~$ config vxlan add vtep 1.1.1.1
create nvo_name (nvo) and bind it to VTEP_name (vtep)
admin@SONIC01:~$ config vxlan evpn_nvo add nvo vtep
Command to map VXLAN VNI to VLAN
admin@SONIC01:~$ config vxlan map add vtep 10 1000
admin@SONIC01:~$ config vxlan map add vtep 30 3000
admin@SONIC01:~$ config save -y
A4630-54PE configuring VTEP_name (vtep) and its IP address
admin@SONIC02:~$ config vxlan add vtep 2.2.2.2
create nvo_name (nvo) and bind it to VTEP_name (vtep)
admin@SONIC02:~$ config vxlan evpn_nvo add nvo vtep
Command to map VXLAN VNI to VLAN
admin@SONIC02:~$ config vxlan map add vtep 20 2000
admin@SONIC02:~$ config vxlan map add vtep 30 3000
admin@SONIC02:~$ config save -y
Configure the layer3 VNI on both switches. AS5835-54X
admin@SONIC01:~$ config vrf add_vrf_vni_map Vrf01 3000
A4630-54PE
admin@SONIC01:~$ config vrf add_vrf_vni_map Vrf01 3000
Verify EVPN-VNI Route Status AS5835-54X
sonic# show evpn vni detail
VNI: 1000
Type: L2
Tenant VRF: Vrf01
VxLAN interface: vtep-10
VxLAN ifIndex: 67
SVI interface: Vlan10
SVI ifIndex: 9
Local VTEP IP: 1.1.1.1
Mcast group: 0.0.0.0
No remote VTEPs known for this VNI
Number of MACs (local and remote) known for this VNI: 1
Number of ARPs (IPv4 and IPv6, local and remote) known for this VNI: 1
Advertise-gw-macip: No
Advertise-svi-macip: No
VNI: 3000
Type: L3
Tenant VRF: Vrf01
Local Vtep Ip: 1.1.1.1
Vxlan-Intf: vtep-30
SVI-If: Vlan30
State: Up
VNI Filter: none
System MAC: 00:a0:c9:00:00:00
Router MAC: 00:a0:c9:00:00:00
L2 VNIs: 1000
A4630-54PE
sonic# show evpn vni detail
VNI: 2000
Type: L2
Tenant VRF: Vrf01
VxLAN interface: vtep-20
VxLAN ifIndex: 78
SVI interface: Vlan20
SVI ifIndex: 76
Local VTEP IP: 2.2.2.2
Mcast group: 0.0.0.0
No remote VTEPs known for this VNI
Number of MACs (local and remote) known for this VNI: 1
Number of ARPs (IPv4 and IPv6, local and remote) known for this VNI: 1
Advertise-gw-macip: No
Advertise-svi-macip: No
VNI: 3000
Type: L3
Tenant VRF: Vrf01
Local Vtep Ip: 2.2.2.2
Vxlan-Intf: vtep-30
SVI-If: Vlan30
State: Up
VNI Filter: none
System MAC: 68:21:5f:29:c0:d2
Router MAC: 68:21:5f:29:c0:d2
L2 VNIs: 2000
Verify BGP Route Summary AS5835-54X
sonic# show bgp summary
IPv4 Unicast Summary (VRF default):
BGP router identifier 188.188.9.14, local AS number 65100 vrf-id 0
BGP table version 17
RIB entries 3, using 552 bytes of memory
Peers 1, using 723 KiB of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd PfxSnt Desc
10.0.0.5 4 65100 1436 1449 0 0 0 03:02:18 1 1 N/A
Total number of neighbors 1
L2VPN EVPN Summary (VRF default):
BGP router identifier 188.188.9.14, local AS number 65100 vrf-id 0
BGP table version 0
RIB entries 27, using 4968 bytes of memory
Peers 1, using 723 KiB of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd PfxSnt Desc
10.0.0.5 4 65100 1436 1449 0 0 0 03:02:18 4 4 N/A
Total number of neighbors 1
A4630-54PE
sonic# show bgp summary
IPv4 Unicast Summary (VRF default):
BGP router identifier 188.188.9.6, local AS number 65100 vrf-id 0
BGP table version 8
RIB entries 3, using 552 bytes of memory
Peers 1, using 723 KiB of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd PfxSnt Desc
10.0.0.4 4 65100 220 221 0 0 0 03:02:18 1 1 N/A
Total number of neighbors 1
L2VPN EVPN Summary (VRF default):
BGP router identifier 188.188.9.6, local AS number 65100 vrf-id 0
BGP table version 0
RIB entries 11, using 2024 bytes of memory
Peers 1, using 723 KiB of memory
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd PfxSnt Desc
10.0.0.4 4 65100 220 221 0 0 0 03:02:18 4 4 N/A
Total number of neighbors 1
Validate EVPN route learning AS5835-54X
sonic# show ip route vrf all
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, F - PBR,
f - OpenFabric,
> - selected route, * - FIB route, q - queued, r - rejected, b - backup
t - trapped, o - offload failure
VRF Vrf01:
C>* 192.168.1.0/24 is directly connected, Vlan10, 03:18:41
K>* 192.168.1.254/32 [0/0] is directly connected, Vlan10, 03:18:41
B>* 192.168.2.0/24 [200/0] via 2.2.2.2, Vlan30 onlink, weight 1, 03:04:24
B>* 192.168.2.2/32 [200/0] via 2.2.2.2, Vlan30 onlink, weight 1, 02:21:18
VRF default:
K>* 0.0.0.0/0 [0/202] via 188.188.1.1, eth0, 22:59:15
K * 1.1.1.1/32 [0/0] is directly connected, Loopback0, 22:54:06
C>* 1.1.1.1/32 is directly connected, Loopback0, 22:54:06
B>* 2.2.2.2/32 [200/0] via 10.0.0.5, Ethernet48, weight 1, 03:04:24
C>* 10.0.0.4/31 is directly connected, Ethernet48, 03:07:18
K>* 10.0.0.4/32 [0/0] is directly connected, Ethernet48, 22:45:24
C>* 188.188.0.0/16 is directly connected, eth0, 22:59:15
sonic# show bgp l2vpn evpn
BGP table version is 14, local router ID is 188.188.9.14
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
EVPN type-1 prefix: [1]:[EthTag]:[ESI]:[IPlen]:[VTEP-IP]
EVPN type-2 prefix: [2]:[EthTag]:[MAClen]:[MAC]:[IPlen]:[IP]
EVPN type-3 prefix: [3]:[EthTag]:[IPlen]:[OrigIP]
EVPN type-4 prefix: [4]:[ESI]:[IPlen]:[OrigIP]
EVPN type-5 prefix: [5]:[EthTag]:[IPlen]:[IP]
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 188.188.9.6:2
*>i[2]:[0]:[48]:[80:a2:35:5a:22:50]
2.2.2.2 100 0 i
RT:65100:2000 ET:8
*>i[2]:[0]:[48]:[80:a2:35:5a:22:50]:[32]:[192.168.2.2]
2.2.2.2 100 0 i
RT:65100:2000 RT:65100:3000 ET:8 Rmac:68:21:5f:29:c0:d2
*>i[3]:[0]:[32]:[2.2.2.2]
2.2.2.2 100 0 i
RT:65100:2000 ET:8
Route Distinguisher: 188.188.9.14:2
*> [2]:[0]:[48]:[b8:6a:97:19:ba:12]
1.1.1.1 32768 i
ET:8 RT:65100:1000
*> [2]:[0]:[48]:[b8:6a:97:19:ba:12]:[32]:[192.168.1.1]
1.1.1.1 32768 i
ET:8 RT:65100:1000 RT:65100:3000 Rmac:00:a0:c9:00:00:00
*> [3]:[0]:[32]:[1.1.1.1]
1.1.1.1 32768 i
ET:8 RT:65100:1000
Route Distinguisher: 192.168.1.254:3
*> [5]:[0]:[24]:[192.168.1.0]
1.1.1.1 0 32768 ?
ET:8 RT:65100:3000 Rmac:00:a0:c9:00:00:00
Route Distinguisher: 192.168.2.254:3
*>i[5]:[0]:[24]:[192.168.2.0]
2.2.2.2 0 100 0 ?
RT:65100:3000 ET:8 Rmac:68:21:5f:29:c0:d2
Displayed 8 out of 8 total prefixes
#A4630-54PE
sonic# show ip route vrf all
Codes: K - kernel route, C - connected, S - static, R - RIP,
O - OSPF, I - IS-IS, B - BGP, E - EIGRP, N - NHRP,
T - Table, v - VNC, V - VNC-Direct, A - Babel, F - PBR,
f - OpenFabric,
> - selected route, * - FIB route, q - queued, r - rejected, b - backup
t - trapped, o - offload failure
VRF Vrf01:
B>* 192.168.1.0/24 [200/0] via 1.1.1.1, Vlan30 onlink, weight 1, 03:04:23
B>* 192.168.1.1/32 [200/0] via 1.1.1.1, Vlan30 onlink, weight 1, 02:20:51
C>* 192.168.2.0/24 is directly connected, Vlan20, 03:07:28
K>* 192.168.2.254/32 [0/0] is directly connected, Vlan20, 03:07:28
VRF default:
K>* 0.0.0.0/0 [0/202] via 188.188.1.1, eth0, 03:17:24
B>* 1.1.1.1/32 [200/0] via 10.0.0.4, Ethernet52, weight 1, 03:04:23
K * 2.2.2.2/32 [0/0] is directly connected, Loopback0, 03:07:29
C>* 2.2.2.2/32 is directly connected, Loopback0, 03:07:29
C>* 10.0.0.4/31 is directly connected, Ethernet52, 03:07:17
K>* 10.0.0.5/32 [0/0] is directly connected, Ethernet52, 03:07:18
C>* 188.188.0.0/16 is directly connected, eth0, 03:17:24
sonic# show bgp l2vpn evpn
BGP table version is 12, local router ID is 188.188.9.6
Status codes: s suppressed, d damped, h history, * valid, > best, i - internal
Origin codes: i - IGP, e - EGP, ? - incomplete
EVPN type-1 prefix: [1]:[EthTag]:[ESI]:[IPlen]:[VTEP-IP]
EVPN type-2 prefix: [2]:[EthTag]:[MAClen]:[MAC]:[IPlen]:[IP]
EVPN type-3 prefix: [3]:[EthTag]:[IPlen]:[OrigIP]
EVPN type-4 prefix: [4]:[ESI]:[IPlen]:[OrigIP]
EVPN type-5 prefix: [5]:[EthTag]:[IPlen]:[IP]
Network Next Hop Metric LocPrf Weight Path
Route Distinguisher: 188.188.9.6:2
*> [2]:[0]:[48]:[80:a2:35:5a:22:50]
2.2.2.2 32768 i
ET:8 RT:65100:2000
*> [2]:[0]:[48]:[80:a2:35:5a:22:50]:[32]:[192.168.2.2]
2.2.2.2 32768 i
ET:8 RT:65100:2000 RT:65100:3000 Rmac:68:21:5f:29:c0:d2
*> [3]:[0]:[32]:[2.2.2.2]
2.2.2.2 32768 i
ET:8 RT:65100:2000
Route Distinguisher: 188.188.9.14:2
*>i[2]:[0]:[48]:[b8:6a:97:19:ba:12]
1.1.1.1 100 0 i
RT:65100:1000 ET:8
*>i[2]:[0]:[48]:[b8:6a:97:19:ba:12]:[32]:[192.168.1.1]
1.1.1.1 100 0 i
RT:65100:1000 RT:65100:3000 ET:8 Rmac:00:a0:c9:00:00:00
*>i[3]:[0]:[32]:[1.1.1.1]
1.1.1.1 100 0 i
RT:65100:1000 ET:8
Route Distinguisher: 192.168.1.254:3
*>i[5]:[0]:[24]:[192.168.1.0]
1.1.1.1 0 100 0 ?
RT:65100:3000 ET:8 Rmac:00:a0:c9:00:00:00
Route Distinguisher: 192.168.2.254:3
*> [5]:[0]:[24]:[192.168.2.0]
2.2.2.2 0 32768 ?
ET:8 RT:65100:3000 Rmac:68:21:5f:29:c0:d2
Displayed 8 out of 8 total prefixes
QoS Configuration
| PICOS | SONiC |
|---|---|
|
# Commands to create QoS classifiers #syntax set class-of–service classifier <classifier-name> delete class-of–service classifier c1 #Example creates a classifier c1 with forwarding-class f1 and code-point 3 set class-of-service classifier c1 forwarding-class f1 code-point 3 # Commands to create QoS schedulers #syntax # Configure scheduling algorithm for queue scheduling. set class-of-service scheduler <scheduler-name> mode <SP | WRR | WFQ> # Configure guaranteed rate and the maximum rate for the interface queue set class-of-service scheduler <scheduler-name> guaranteed-rate <value> set class-of-service scheduler <scheduler-name> max-rate <value> # Configure scheduler profile associated with the configured scheduler and forwarding class. set class-of-service scheduler-profile <scheduler-profile-name> forwarding-class <forwarding-class-name> scheduler <scheduler-name> # Configure mapping between forwarding class and local priority. set class-of-service forwarding-class <forwarding-class-name> local-priority <int> # Apply the scheduler profile to an egress interface. set class-of-service interface <interface-name> scheduler-profile <scheduler-profile-name> |
# Commands to create QoS classifiers ( Edge core SONiC Platform - AS9716-32D) #Syntax Create a profile for DOT1P/DSCP mapped to TC(Traffic Class). #Example for DSCP config qos dscp-tc add DSCP_TC --dscp 7 --tc 1 #Modify the existing Dot1p/DSCP to TC profile. #Example for DOT1P: config qos dot1p-tc update 1p_tc --dot1p 1 --tc 2 #Validate the profile for DOT1P/DSCP to Traffic class. # DOT1P to TC: show qos dot1p-tc #Validate Queue mapping from DSCP queue to Traffic class show qos dscp-tc # Create a profile for traffic class and map it to Queue config qos tc-queue add TC_Q --tc 1 --queue 2 # Validate the profile of Traffic class to Queue. show qos tc-queue #Binding the mapping table to the specified interface. config interface qos dscp-tc bind Ethernet0 DSCP_TC #Validate the binding table. show interfaces qos # Clear the queue counter sonic-clear queue counters #Check Specific ethernet port (egress port) queue counters show queue counters Ethernet8 # Marking configuration #Create a profile for DOT1P remarking. #Example for Dot1P: config qos remark dot1p add remark_dot1p --tc 0 --dot1p 1 # Validate the remark profile. show qos remark dot1p # Bind the remark table to the egress interface. config interface qos remark dot1p bind Ethernet8 remark_dot1p #Validate the binding table. show interfaces qos # Scheduler Configuration(Edge Core SONiC platform - AS7326-56X) # Set the scheduler mode. config scheduler add strict_mode --sched_type STRICT # Validate scheduler status. show scheduler # Bind the scheduler to ethernet sub- interface. >#Example config interface scheduler bind queue Ethernet 5.3 strict_mode #Command to unbind the scheduler from ethernet interface config interface scheduler unbind queue Ethernet 5.3 #Validate scheduler status. show interfaces scheduler #Validate Scheduler queues show queue counters Ethernet5 # Set the scheduler mode #Example config scheduler add wrr_7 --sched_type WRR --weight 7 config scheduler add wrr_3 --sched_type WRR --weight 3 #validate scheduler status. show scheduler # Bind the scheduler to ethernet interface. #Example config interface scheduler bind queue Ethernet5 3 wrr_7 config interface scheduler bind queue Ethernet5 4 wrr_3 # validate scheduler status. show interfaces scheduler |
ACL Configuration
| PICOS | SONiC |
|---|---|
|
# Command to create ACL rules #syntax set firewall filter MyFilter sequence set firewall filter <filter-name> sequence <number> then action discard set firewall filter <filter-name> sequence <number> from destination-address-ipv6 <ipv6_address> set firewall filter <filter-name> sequence <number> then action forward set firewall filter<filter-name1> sequence <number1> from source-address-ipv4 <source_ip_address> set firewall filter bad-net sequence <number1> then action discard |
# Command to create ACL Tables # Syntax config acl add table <ACL_table_name> L3 --description 'ACL_Test1' --stage 'ingress' --ports 'Ethernet<number>’' # Example config acl add table ACL_Test1 L3V6 --description 'ACL_Test1' --stage 'egress' --ports 'Ethernet16' #Command to delete ACL tables config acl remove table <ACL_Table_Name> #Command to create ACL Rule with source_ip_address #Example config acl add rule --src-ip4 100.0.0.1 --priority 3 ACL_Test1 deny # Commands to verify ACL table and rule created - show acl table show acl rule |
References
- https://docs.pica8.com/
- https://support.edge-core.com/hc/en-us/articles/900004369066--Enterprise-SONiC-OSPF-Open-Shortest-Path-First-
- https://support.edge-core.com/hc/en-us/articles/900000789566--Enterprise-SONiC-BGP-Step-1-Establish-BGP-Session
- https://support.edge-core.com/hc/en-us/articles/900000809363--Enterprise-SONiC-BGP-Step-2-1-Redistribute-routes-to-BGP-process-Optional-
- https://support.edge-core.com/hc/en-us/articles/900002377366--Enterprise-SONiC-BGP-Unnumbered
- https://support.edge-core.com/hc/en-us/articles/900004277226--Enterprise-SONiC-VRF-Virtual-routing-and-forwarding-
- https://support.edge-core.com/hc/en-us/articles/900002380706--Enterprise-SONiC-MC-LAG
- https://support.edge-core.com/hc/en-us/articles/900002741223--Enterprise-SONiC-Symmetric-EVPN-IRB
- https://support.edge-core.com/hc/en-us/articles/900002720523--Enterprise-SONiC-EVPN-L2-VxLAN
- https://support.edge-core.com/hc/en-us/articles/900000214926--Enterprise-SONiC-ACL-Access-Control-List-
- https://support.edge-core.com/hc/en-us/articles/9391323739417--Enterprise-SONiC-ZTP-Zero-Touch-Provisioning-
- https://support.edge-core.com/hc/en-us/articles/900000240066--Enterprise-SONiC-QoS-Quality-of-Service-
- https://support.edge-core.com/hc/en-us/articles/900000198943--Enterprise-SONiC-DHCP-Relay
- https://support.edge-core.com/hc/en-us/articles/900000307246--Enterprise-SONiC-SONiC-overview
- https://support.edge-core.com/hc/en-us/articles/900004277226--Enterprise-SONiC-VRF-Virtual-routing-and-forwarding-
- https://support.edge-core.com/hc/en-us/articles/900000214266--Enterprise-SONiC-LLDP-Link-Layer-Discovery-Protocol-
- https://support.edge-core.com/hc/en-us/articles/900007074363--Enterprise-SONiC-Sub-Interface